The attacker maliciously accessed the user’s PC and encrypted specific volumes. How to decrypt the volume?
解法1
下载下来文件,010 editor打开,发现7z文件头,解压后得到secret和memory。
看wp说是bitlocker文件。
先用volatility分析下memory
Volatility Foundation Volatility Framework 2.6INFO : volatility.debug : Determining profile based on KDBG search...Suggested Profile(s) : Win7SP1x86_23418, Win7SP0x86, Win7SP1x86AS Layer1 : IA32PagedMemoryPae (Kernel AS)AS Layer2 : FileAddressSpace (D:\Download\强网杯\MISC\CipherMan\附件\CipherMan~\memory)PAE type : PAEDTB : 0x185000LKDBG : 0x82d72c28LNumber of Processors : 1Image Type (Service Pack) : 1KPCR for CPU 0 : 0x82d73c00LKUSER_SHARED_DATA : 0xffdf0000LImage date and time : 2018-08-06 08:41:18 UTC+0000Image local date and time : 2018-08-06 17:41:18 +0900
然后查看桌面下的文件:
Volatility Foundation Volatility Framework 2.60x000000007ca92050 8 0 R--r-- \Device\HarddiskVolume2\Windows\System32\catroot\{F750E6C3-38EE-11D1-85E5-00C04FC295EE}\Microsoft-Windows-DesktopWindowManager-uDWM-Package~31bf3856ad364e35~x86~~6.1.7601.17514.cat0x000000007ca92968 8 0 R--r-- \Device\HarddiskVolume2\Windows\System32\catroot\{F750E6C3-38EE-11D1-85E5-00C04FC295EE}\Microsoft-Windows-DesktopWindowManager-uDWM-Package~31bf3856ad364e35~x86~~6.1.7600.16385.cat0x000000007d105990 8 0 R--r-- \Device\HarddiskVolume2\Windows\System32\catroot\{F750E6C3-38EE-11D1-85E5-00C04FC295EE}\Microsoft-Windows-Display-ChangeDesktopBackground-Disabled-Package~31bf3856ad364e35~x86~~6.1.7600.16385.cat0x000000007df334f0 2 0 R--rwd \Device\HarddiskVolume2\Users\RockAndRoll\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Accessories\Accessibility\Desktop.ini0x000000007df335a8 2 0 R--rwd \Device\HarddiskVolume2\Users\RockAndRoll\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Accessories\System Tools\Desktop.ini0x000000007df33660 2 0 R--rwd \Device\HarddiskVolume2\ProgramData\Microsoft\Windows\Start Menu\Programs\Accessories\System Tools\Desktop.ini0x000000007df33910 2 0 R--rwd \Device\HarddiskVolume2\ProgramData\Microsoft\Windows\Start Menu\Programs\Accessories\Desktop.ini0x000000007df33a80 2 0 R--rwd \Device\HarddiskVolume2\Users\RockAndRoll\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Maintenance\Desktop.ini0x000000007df34f80 2 0 R--rwd \Device\HarddiskVolume2\Users\RockAndRoll\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Accessories\Desktop.ini0x000000007df36800 2 0 R--rwd \Device\HarddiskVolume2\ProgramData\Microsoft\Windows\Start Menu\Programs\Maintenance\Desktop.ini0x000000007df36e18 2 0 R--rwd \Device\HarddiskVolume2\ProgramData\Microsoft\Windows\Start Menu\Programs\Games\Desktop.ini0x000000007df3e548 2 1 R--rwd \Device\HarddiskVolume2\Users\Public\Desktop0x000000007df3e820 2 1 R--rwd \Device\HarddiskVolume2\Users\Public\Desktop0x000000007df3eab8 2 1 R--rwd \Device\HarddiskVolume2\Users\RockAndRoll\Desktop0x000000007df3f4a8 2 1 R--rwd \Device\HarddiskVolume2\Users\RockAndRoll\Desktop0x000000007e02af80 8 0 -W---- \Device\HarddiskVolume2\Users\RockAndRoll\Desktop\BitLocker ??? ??168F1291-82C1-4BF2-B634-9CCCEC63E9ED.txt0x000000007e61f268 2 0 R--rwd \Device\HarddiskVolume2\ProgramData\Microsoft\Windows\Start Menu\Programs\Accessories\Tablet PC\Desktop.ini0x000000007e61f718 2 0 R--rwd \Device\HarddiskVolume2\ProgramData\Microsoft\Windows\Start Menu\Programs\Accessories\Accessibility\Desktop.ini0x000000007e7e1310 8 0 R--rwd \Device\HarddiskVolume2\Users\RockAndRoll\Links\Desktop.lnk0x000000007eaf5198 8 0 R--rw- \Device\HarddiskVolume2\Users\Public\Desktop\Messenger Center.lnk0x000000007eaf5290 8 0 R--rw- \Device\HarddiskVolume2\Users\Public\Desktop\Media Player Center.lnk0x000000007eea3760 8 0 R--r-- \Device\HarddiskVolume2\Windows\System32\catroot\{F750E6C3-38EE-11D1-85E5-00C04FC295EE}\Microsoft-Windows-Display-ChangeDesktopBackground-Disabled-Package~31bf3856ad364e35~x86~~6.1.7601.17514.cat0x000000007eed7a68 8 0 R--rwd \Device\HarddiskVolume2\Users\Public\Desktop\desktop.ini0x000000007f534cd8 8 0 R--rwd \Device\HarddiskVolume2\Users\RockAndRoll\Desktop\desktop.ini
可以看到有Bitlocker关键字:
提取出来看下: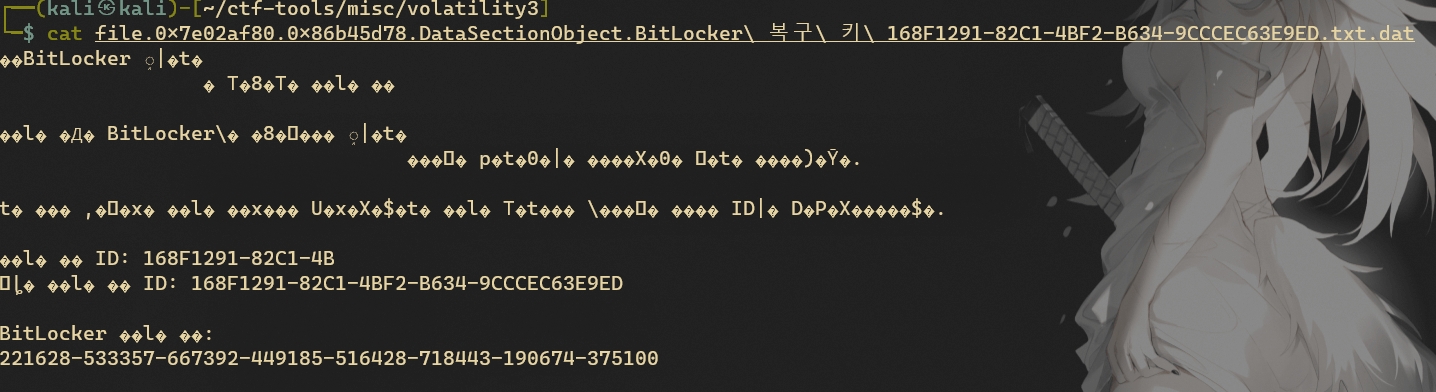
虽然乱码了,但还是可以看出来是Bitlocker的密钥。
用Elecomsoft Forenisc Disk Decryptor解密Secret文件。
解密后挂载,打开后发现有个README.txt
内容就是flag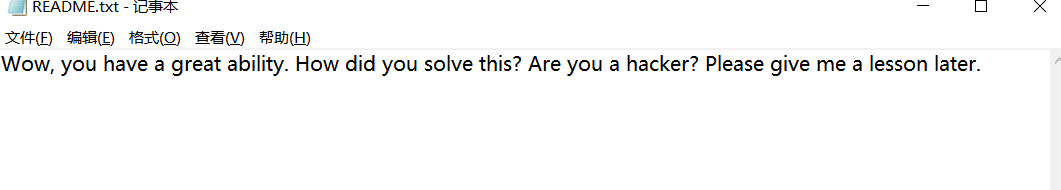
解法2
bitlocker加密后的硬盘都会有一个-FVE-FS-标志,010 editor打开后搜索,发现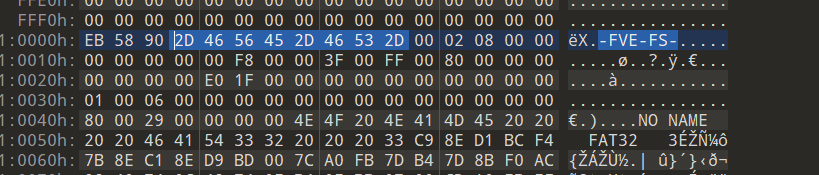
确定是bitlocker,使用插件https://github.com/elceef/bitlocker
直接读取bitlocker密钥
volatility -f memory --profile Win7SP1x86_23418 bitlockerVolatility Foundation Volatility Framework 2.6Address : 0x86863bc8Cipher : AES-128FVEK : 7c9e29b3708f344e4041271dc54175c5TWEAK : 4e3ef340dd377cea9c643951ce1e56c6
用Elecomsoft Forenisc Disk Decryptor解密Secret文件,拿到README.txt。

