下载下载文件,volatility扫一下命令行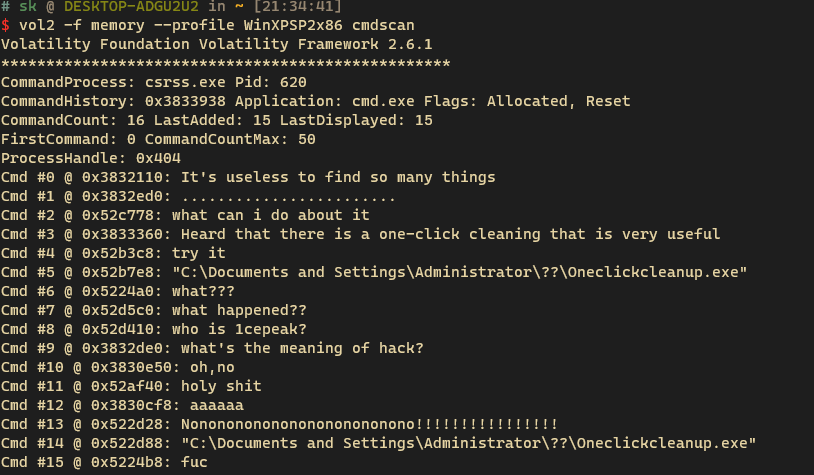
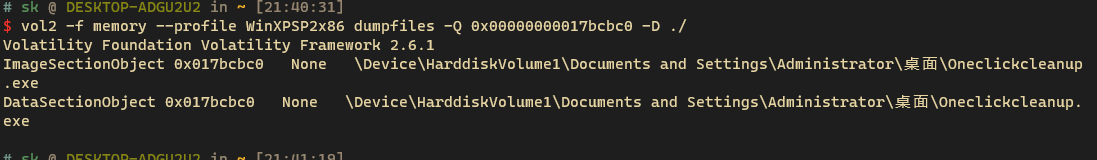
找到Oneclickcleanup.exe,导出来,进入逆向环节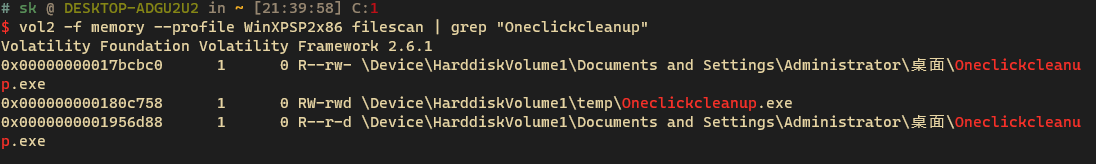
int __cdecl main(int argc, const char **argv, const char **envp){FILE *v4; // [esp+10h] [ebp-14h]int k; // [esp+14h] [ebp-10h]signed int j; // [esp+18h] [ebp-Ch]int i; // [esp+1Ch] [ebp-8h]__main();for ( i = 0; i <= 44; ++i )_data_start__[i] ^= key[i % 10];for ( j = 0; j < (int)size; ++j )data[j] ^= key[j % 10];for ( k = 0; k <= 9; ++k )puts("Hacked by 1cePack!!!!!!!");v4 = fopen(_data_start__, "wb+");fwrite(data, size, 1u, v4);return 0;}
代码还是很简单的,就是对两块数据进行异或,最后写到文件里。
datastart中的数据是文件名,就不管了,主要看data的数据。
写脚本跑一下:
key = "this_a_key"for i in range(len(data)):data[i]=data[i]^ord(key[i%10])with open("file",'wb') as file:for i in data:file.write(chr(i).encode('utf-8'))
010 editor打开文件,发现Sub MAIN和word6.0字样,猜测为word6.0宏病毒样本,解密宏代码。
doc宏加密方式为opcode异或,且opcode长度为1字节取值为0-65535,对提取出的文档进行异或解密爆破,在opcode为0x2d,得到flag
from Crypto.Util.number import long_to_bytes as l2bori = b''with open('file','rb') as f:ori = f.read()for opcode in range(0x00,0xff):data = b''for i in ori:data += l2b(i ^ opcode)if b'flag{' in data:print(data[data.index(b'flag{'):])

