JWT整合SpringBoot
在整合SpringBoot之前,我们先封装好一个JWT的工具类,方便调用:
public class JWTUtils {private static String TOKEN = "token!Q@W3e4r";/*** 生成token* @param map //传入payload* @return 返回token*/public static String getToken(Map<String,String> map){JWTCreator.Builder builder = JWT.create();map.forEach((k,v)->{builder.withClaim(k,v);});Calendar instance = Calendar.getInstance();instance.add(Calendar.SECOND,7);builder.withExpiresAt(instance.getTime());return builder.sign(Algorithm.HMAC256(TOKEN)).toString();}/*** 验证token* @param token* @return*/public static void verify(String token){JWT.require(Algorithm.HMAC256(TOKEN)).build().verify(token);}/*** 获取token中payload* @param token* @return*/public static DecodedJWT getToken(String token){return JWT.require(Algorithm.HMAC256(TOKEN)).build().verify(token);}}
整合SpringBoot
导入依赖:
<!--引入jwt--><dependency><groupId>com.auth0</groupId><artifactId>java-jwt</artifactId><version>3.4.0</version></dependency><!--引入mybatis--><dependency><groupId>org.mybatis.spring.boot</groupId><artifactId>mybatis-spring-boot-starter</artifactId><version>2.1.3</version></dependency><!--引入lombok--><dependency><groupId>org.projectlombok</groupId><artifactId>lombok</artifactId><version>1.18.12</version></dependency><!--引入druid--><dependency><groupId>com.alibaba</groupId><artifactId>druid</artifactId><version>1.1.19</version></dependency><!--引入mysql--><dependency><groupId>mysql</groupId><artifactId>mysql-connector-java</artifactId><version>5.1.38</version></dependency>
编写配置文件:
server.port=8989spring.application.name=jwtspring.datasource.type=com.alibaba.druid.pool.DruidDataSourcespring.datasource.driver-class-name=com.mysql.jdbc.Driverspring.datasource.url=jdbc:mysql://localhost:3306/jwt?characterEncoding=UTF-8spring.datasource.username=rootspring.datasource.password=rootmybatis.type-aliases-package=com.zym.pojomybatis.mapper-locations=classpath:com.zym.mapper.*.xmllogging.level.com.baizhi.dao=debug
数据库:
DROP TABLE IF EXISTS `user`;CREATE TABLE `user` (`id` int(11) NOT NULL AUTO_INCREMENT COMMENT '主键',`name` varchar(80) DEFAULT NULL COMMENT '用户名',`password` varchar(40) DEFAULT NULL COMMENT '用户密码',PRIMARY KEY (`id`)) ENGINE=InnoDB AUTO_INCREMENT=2 DEFAULT CHARSET=utf8;
User:
@Data@Accessors(chain=true)public class User {private String id;private String name;private String password;}
UserMapper与UserMapper.xml
@Mapperpublic interface UserDAO {User login(User user);}
<?xml version="1.0" encoding="UTF-8" ?><!DOCTYPE mapperPUBLIC "-//mybatis.org//DTD Mapper 3.0//EN""http://mybatis.org/dtd/mybatis-3-mapper.dtd"><mapper namespace="com.zym.mapper.UserMapper"><select id="login" resultType="com.zym.springboot_jwt.pojo.User">select * from User where name = #{name} and password = #{password};</select></mapper>
UserService:
public interface UserService {User login(User user);//登录接口}
UserServiceImpl:
@Service@Transactionalpublic class UserServiceImpl implements UserService {@Autowiredprivate UserDAO userDAO;@Override@Transactional(propagation = Propagation.SUPPORTS)public User login(User user) {User userDB = userDAO.login(user);if(userDB!=null){return userDB;}throw new RuntimeException("登录失败~~");}}
UserController:
@RestController@Slf4jpublic class UserController {@Autowiredprivate UserService userService;@GetMapping("/user/login")public Map<String,Object> login(User user) {Map<String,Object> result = new HashMap<>();log.info("用户名: [{}]", user.getName());log.info("密码: [{}]", user.getPassword());try {User userDB = userService.login(user);Map<String, String> map = new HashMap<>();//用来存放payloadmap.put("id",userDB.getId());map.put("username", userDB.getName());String token = JWTUtils.getToken(map);result.put("state",true);result.put("msg","登录成功!!!");result.put("token",token); //成功返回token信息} catch (Exception e) {e.printStackTrace();result.put("state","false");result.put("msg",e.getMessage());}return result;}}
测试一下: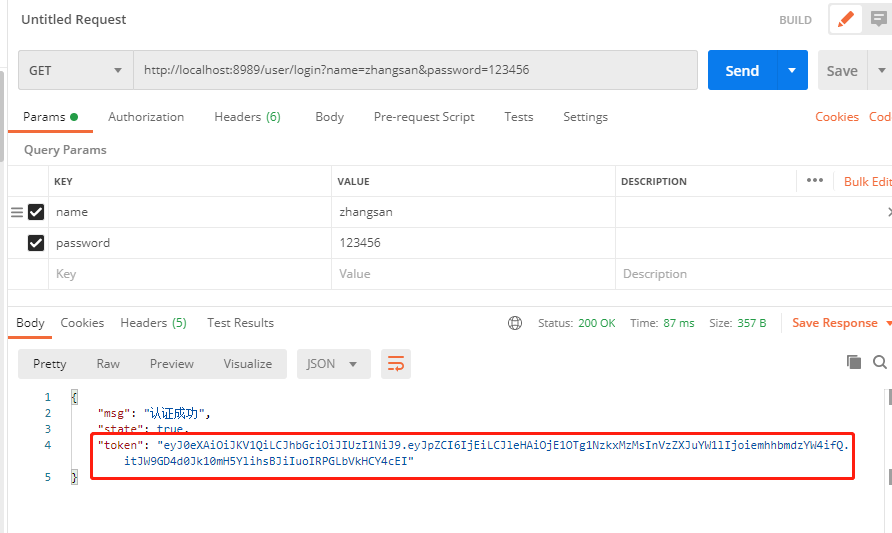
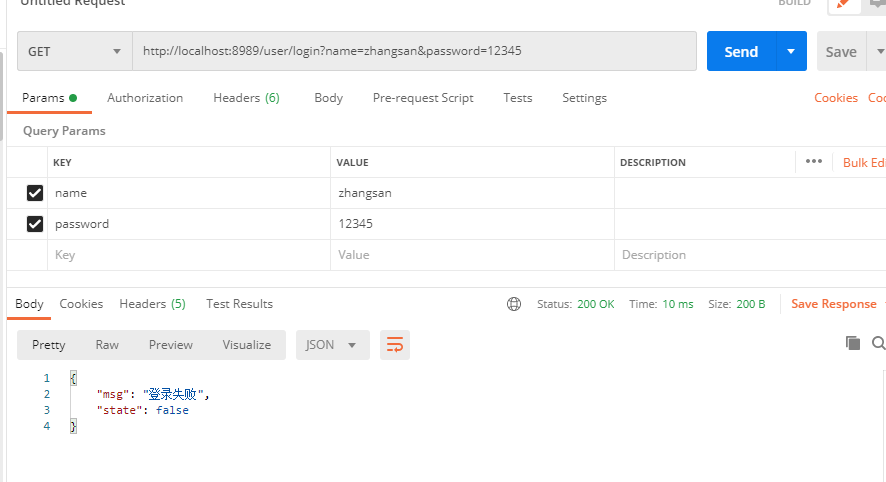
再测试一下验证Token的接口:
@PostMapping("/user/test")public Map<String, Object> test(String token){Map<String,Object> map = new HashMap<>();log.info("当前Token为[{}]",token);try{DecodedJWT decodedJWT = JWTUtils.verify(token);//验证令牌map.put("state",true);map.put("msg","请求成功");return map;}catch (SignatureVerificationException e){e.printStackTrace();map.put("msg","无效签名");}catch (TokenExpiredException e){e.printStackTrace();map.put("msg","token过期");}catch (AlgorithmMismatchException e){e.printStackTrace();map.put("msg","算法不一致");}catch (Exception e){e.printStackTrace();map.put("msg","token无效");}map.put("state",false);return map;}
发送正确的token: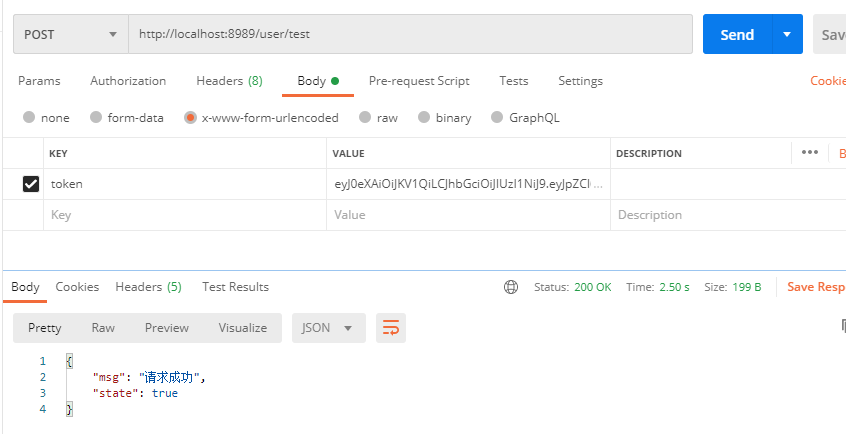
发送错误或者不发生token: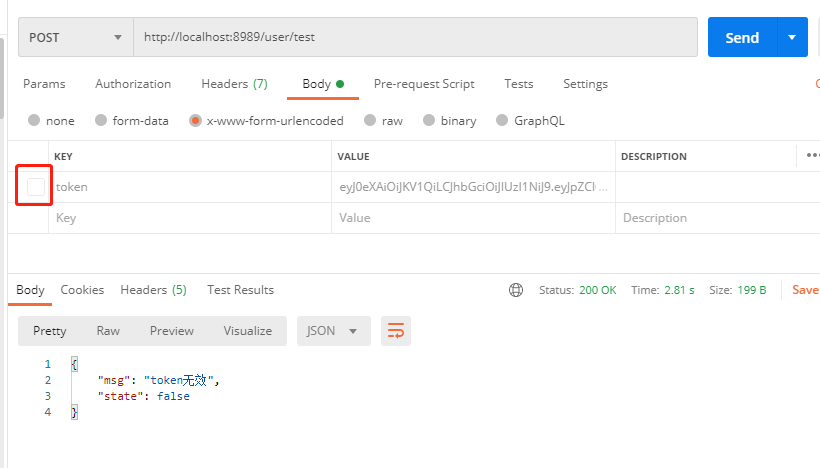
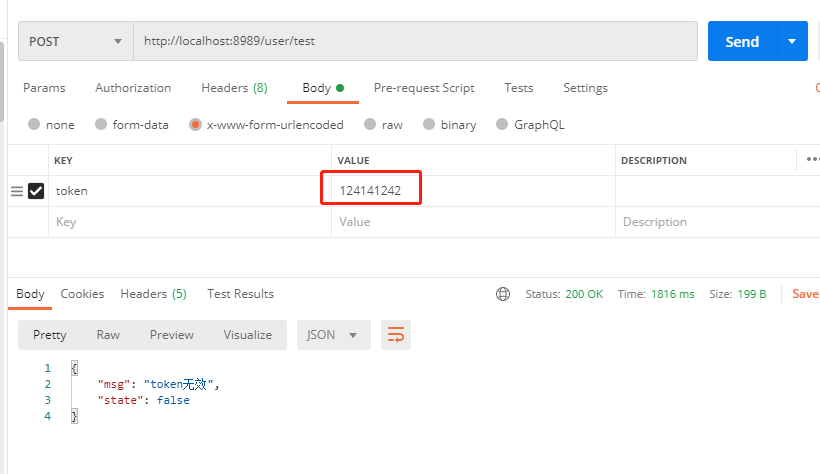
但是这样很麻烦,明天我们把验证的过程放到拦截器里,实现真实业务场景常用的样子

