一键生成密钥
自动生成authorized_keys 复制一份给自己
[chroot@ntp-server-it-ap02 .ssh]$ ssh-copy-id ntp-server-it-ap02/usr/bin/ssh-copy-id: INFO: Source of key(s) to be installed: "/home/chroot/.ssh/id_rsa.pub"The authenticity of host 'ntp-server-it-ap02 (10.82.100.81)' can't be established.ECDSA key fingerprint is SHA256:YL7wjH4GtBLMgsgqXVg9lb0ga4pdVr0ENgFnESi7Nsc.Are you sure you want to continue connecting (yes/no/[fingerprint])? yes/usr/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed/usr/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to install the new keys/etc/ssh/ssh_config line 59: Unsupported option "gssapiauthentication"Be sure you are authorized to access this system!chroot@ntp-server-it-ap02's password:Number of key(s) added: 1Now try logging into the machine, with: "ssh 'ntp-server-it-ap02'"and check to make sure that only the key(s) you wanted were added.[chroot@ntp-server-it-ap02 .ssh]$ ls -ltotal 16-rw------- 1 chroot chroot 579 Jan 9 10:28 authorized_keys-rw------- 1 chroot chroot 2610 Jan 9 10:09 id_rsa-rw-r--r-- 1 chroot chroot 579 Jan 9 10:09 id_rsa.pub-rw-r--r-- 1 chroot chroot 1158 Jan 9 10:28 known_hosts[chroot@ntp-server-it-ap02 .ssh]$
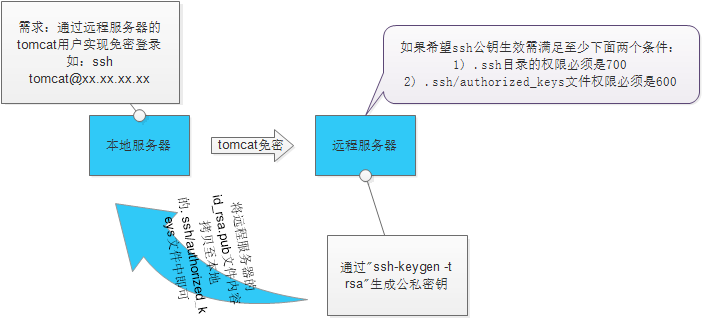
手动生成权限设置
chmod 700 ~/.ssh
chmod 644 ~/.ssh/authorized_keys
[chroot@ntp-server-it-ap02 .ssh]$ ssh-keygen -t rsaGenerating public/private rsa key pair.Enter file in which to save the key (/home/chroot/.ssh/id_rsa):Enter passphrase (empty for no passphrase):Enter same passphrase again:Your identification has been saved in /home/chroot/.ssh/id_rsaYour public key has been saved in /home/chroot/.ssh/id_rsa.pubThe key fingerprint is:SHA256:nn24ysqxCkUv40izxDyijeF9+xhyDi81bf9mGVBEtoo chroot@ntp-server-it-ap02The key's randomart image is:+---[RSA 3072]----+| o+ || ... || . .. || o . . ... ||o B + oES.. ||oB.B = + o o ||o.=+o++ + o + || oB.++ . * || o*=oo.=. |+----[SHA256]-----+[chroot@ntp-server-it-ap02 .ssh]$ ls -ltotal 12-rw------- 1 chroot chroot 2610 Jan 9 10:09 id_rsa-rw-r--r-- 1 chroot chroot 579 Jan 9 10:09 id_rsa.pub-rw-r--r-- 1 chroot chroot 978 Jan 8 20:06 known_hosts[chroot@ntp-server-it-ap02 .ssh]$[chroot@ntp-server-it-ap02 .ssh]$ cat authorized_keysssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDAbmdeqsIjjItnKhpW4cbGHBO4CCp7s0sj3Jl0aD9ERJ0AcbofejvcPmWBFxC2UdQdQF4fcSy/9j3u5l0gxkq5XGDmVwi5hgPGgAMXNd2hJEbtRFHKeNeDN5n0dFzSWTojpFsHEHitQdxMYtGokUxcvUeFzpX6ZR169kQtRknB0srzqoaaeJz9RcjGIolVjGWlpWXm2cWjAE5EU/npxXmilbEh9yZkd0HypaeLw7UG1Ki3I3L5nHBb/n4HjDhu+lw5WA0ipuJ1RrPI7+V+1W+aTNwglTwjLJ4cZ8Gj/nOPJ0Ht4+6eBmfymAP5cNWPP/4zmZpLOMz/ns27hud4Eb91R2YbjgmxL0qwH5IGvMEYPU9+ZJW5DVCsH5hQw0OwRgPZXQDagzkWqx92EKlJj59uIS7rs7tiMu+y7mtAH8c53K2Mv+tZgGxKUCp/u/GhFM/HtVQuKWteVKf5u5kLg604utCsGBMi4DBFuNwqtHlM7KX4/+KbV/iHOeKcsOP3k7k= chroot@ntp-server-it-ap02[chroot@ntp-server-it-ap02 .ssh]$ cat id_rsa.pubssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDAbmdeqsIjjItnKhpW4cbGHBO4CCp7s0sj3Jl0aD9ERJ0AcbofejvcPmWBFxC2UdQdQF4fcSy/9j3u5l0gxkq5XGDmVwi5hgPGgAMXNd2hJEbtRFHKeNeDN5n0dFzSWTojpFsHEHitQdxMYtGokUxcvUeFzpX6ZR169kQtRknB0srzqoaaeJz9RcjGIolVjGWlpWXm2cWjAE5EU/npxXmilbEh9yZkd0HypaeLw7UG1Ki3I3L5nHBb/n4HjDhu+lw5WA0ipuJ1RrPI7+V+1W+aTNwglTwjLJ4cZ8Gj/nOPJ0Ht4+6eBmfymAP5cNWPP/4zmZpLOMz/ns27hud4Eb91R2YbjgmxL0qwH5IGvMEYPU9+ZJW5DVCsH5hQw0OwRgPZXQDagzkWqx92EKlJj59uIS7rs7tiMu+y7mtAH8c53K2Mv+tZgGxKUCp/u/GhFM/HtVQuKWteVKf5u5kLg604utCsGBMi4DBFuNwqtHlM7KX4/+KbV/iHOeKcsOP3k7k= chroot@ntp-server-it-ap02[chroot@ntp-server-it-ap02 .ssh]$
https://www.cnblogs.com/isme-zjh/p/11596648.html
一、authorized_keys
1、就是为了让两个linux机器之间使用ssh不需要用户名和密码。采用了数字签名RSA或者DSA来完成这个操作
2、模型分析
假设 A (192.168.20.59)为客户机器,B(192.168.20.60)为目标机;
要达到的目的:
A机器ssh登录B机器无需输入密码;
加密方式选 rsa|dsa均可以,默认dsa
单向登陆的操作过程(能满足上边的目的):
1、登录A机器
2、ssh-keygen -t [rsa|dsa],将会生成密钥文件和私钥文件 id_rsa,id_rsa.pub或id_dsa,id_dsa.pub
3、将 .pub 文件复制到B机器的 .ssh 目录, 并 cat id_dsa.pub >> ~/.ssh/authorized_keys
4、大功告成,从A机器登录B机器的目标账户,不再需要密码了;(直接运行 #ssh 192.168.20.60 )
双向登陆的操作过程:
1、ssh-keygen做密码验证可以使在向对方机器上ssh ,scp不用使用密码.具体方法如下:
2、两个节点都执行操作:#ssh-keygen -t rsa
然后全部回车,采用默认值.
3、这样生成了一对密钥,存放在用户目录的~/.ssh下。
将公钥考到对方机器的用户目录下,并将其复制到~/.ssh/authorized_keys中(操作命令:#cat id_dsa.pub >> ~/.ssh/authorized_keys)。
二、id_rsa、id_rsa.pub
上班的第一天,上司大哥都会说:待会给我发个公钥吧。
这里说的公钥其实就是id_rsa.pub。
上司大哥是要把我们的客户端公钥上传到服务器,然后再把这个客户端公钥添加到authorized_keys。添加后,服务器就会认为你这个客户端为可信任。你则可以访问这个服务器了。
本地主机在 ~/.ssh 键入
ssh-keygen
//会出现两个文件 后缀.pub就是公钥 另一个就是私钥
ssh-copy-id {username}@ip
//就会将公钥上传到服务器之后就可以登陆的

