password requisite pam_cracklib.so retry=5 difok=3 minlen=12 lcredit=-1 ucredit=-1 dcredit=-1 ocredit=-1
[liwm@riyimei ~]$ cat /etc/pam.d/system-auth#%PAM-1.0# This file is auto-generated.# User changes will be destroyed the next time authconfig is run.auth required pam_env.soauth required pam_faildelay.so delay=2000000auth sufficient pam_unix.so nullok try_first_passauth requisite pam_succeed_if.so uid >= 1000 quiet_successauth required pam_deny.soaccount required pam_unix.soaccount sufficient pam_localuser.soaccount sufficient pam_succeed_if.so uid < 1000 quietaccount required pam_permit.sopassword requisite pam_pwquality.so try_first_pass local_users_only retry=3 authtok_type=password sufficient pam_unix.so sha512 shadow nullok try_first_pass use_authtokpassword required pam_deny.sosession optional pam_keyinit.so revokesession required pam_limits.so-session optional pam_systemd.sosession [success=1 default=ignore] pam_succeed_if.so service in crond quiet use_uidsession required pam_unix.sopassword requisite pam_cracklib.so retry=5 difok=3 minlen=12 lcredit=-1 ucredit=-1 dcredit=-1 ocredit=-1[liwm@riyimei ~]$ passwdChanging password for user liwm.Changing password for liwm.(current) UNIX password:New password:BAD PASSWORD: The password fails the dictionary check - it is too simplistic/systematicNew password:BAD PASSWORD: The password fails the dictionary check - it is based on a dictionary wordNew password:BAD PASSWORD: The password is too similar to the old onepasswd: Have exhausted maximum number of retries for service[liwm@riyimei ~]$
策略对root用户不生效
[root@dev-yum-server ~]# passwdChanging password for user root.New password:BAD PASSWORD: The password fails the dictionary check - it is too simplistic/systematicRetype new password:passwd: all authentication tokens updated successfully.[root@dev-yum-server ~]#[root@dev-yum-server ~]# passwdChanging password for user root.New password:[root@dev-yum-server ~]# passwdChanging password for user root.New password:BAD PASSWORD: The password fails the dictionary check - it is based on a dictionary wordRetype new password:passwd: all authentication tokens updated successfully.[root@dev-yum-server ~]#
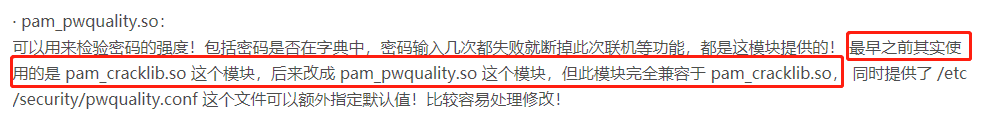

pam_pwquality.so是兼容pam_cracklib.so模块的,所以pam_cracklib.so的选项也适用于pam_pwquality.so
pam_cracklib.so支持的部分选项如下:
retry=N:定义登录/修改密码失败时,可以重试的次数
minlen=N:新密码的最小长度
dcredit=N:当N>0时表示新密码中数字出现的最多次数;当N<0时表示新密码中数字出现最少次数;
ucredit=N: 当N>0时表示新密码中大写字母出现的最多次数;当N<0时表示新密码中大写字母出现最少次数;
lcredit=N: 当N>0时表示新密码中小写字母出现的最多次数;当N<0时表示新密码中小写字母出现最少次数;
ocredit=N:当N>0时表示新密码中特殊字符出现的最多次数;当N<0时表示新密码中特殊字符出现最少次数;
maxrepeat=N:拒绝包含多于N个相同连续字符的密码。 默认值为0表示禁用此检查
maxsequence=N:拒绝包含长于N的单调字符序列的密码。默认值为0表示禁用此检查。实例是’12345’或’fedcb’。除非序列只是密码的一小部分,否则大多数此类密码都不会通过简单检查。
enforce_for_root: 如果用户更改密码是root,则模块将在失败检查时返回错误。默认情况下,此选项处于关闭状态,只打印有关失败检查的消息,但root仍可以更改密码。不要求root用户输入旧密码,因此不会执行比较旧密码和新密码的检查
对root 也控制设置
password requisite pam_pwquality.so minlen=8 dcredit=-2 ucredit=-1 lcredit=-1 ocredit=-1 enforce_for_root try_first_pass local_users_only retry=3 authtok_type=
[root@riyimei ~]# cat /etc/pam.d/system-auth#%PAM-1.0# This file is auto-generated.# User changes will be destroyed the next time authconfig is run.auth required pam_env.soauth required pam_faildelay.so delay=2000000auth sufficient pam_unix.so nullok try_first_passauth requisite pam_succeed_if.so uid >= 1000 quiet_successauth required pam_deny.soaccount required pam_unix.soaccount sufficient pam_localuser.soaccount sufficient pam_succeed_if.so uid < 1000 quietaccount required pam_permit.sopassword requisite pam_pwquality.so minlen=8 dcredit=-2 ucredit=-1 lcredit=-1 ocredit=-1 enforce_for_root try_first_pass local_users_only retry=3 authtok_type=password sufficient pam_unix.so sha512 shadow nullok try_first_pass use_authtokpassword required pam_deny.sosession optional pam_keyinit.so revokesession required pam_limits.so-session optional pam_systemd.sosession [success=1 default=ignore] pam_succeed_if.so service in crond quiet use_uidsession required pam_unix.so#password requisite pam_cracklib.so retry=5 difok=3 minlen=12 lcredit=-1 ucredit=-1 dcredit=-1 ocredit=-1#password required pam_cracklib.so dcredit=-1 ucredit=-1 ocredit=-1 lcredit=0 minlen=8 enforce_for_root[root@riyimei ~]#
password required pam_cracklib.so dcredit=-1 ucredit=-1 ocredit=-1 lcredit=0 minlen=8 enforce_for_root
[root@riyimei ~]# cat /etc/pam.d/system-auth#%PAM-1.0# This file is auto-generated.# User changes will be destroyed the next time authconfig is run.auth required pam_env.soauth required pam_faildelay.so delay=2000000auth sufficient pam_unix.so nullok try_first_passauth requisite pam_succeed_if.so uid >= 1000 quiet_successauth required pam_deny.soaccount required pam_unix.soaccount sufficient pam_localuser.soaccount sufficient pam_succeed_if.so uid < 1000 quietaccount required pam_permit.so#password requisite pam_pwquality.so minlen=8 dcredit=-2 ucredit=-1 lcredit=-1 ocredit=-1 enforce_for_root try_first_pass local_users_only retry=3 authtok_type=password sufficient pam_unix.so sha512 shadow nullok try_first_pass use_authtokpassword required pam_deny.sosession optional pam_keyinit.so revokesession required pam_limits.so-session optional pam_systemd.sosession [success=1 default=ignore] pam_succeed_if.so service in crond quiet use_uidsession required pam_unix.so#password requisite pam_cracklib.so retry=5 difok=3 minlen=12 lcredit=-1 ucredit=-1 dcredit=-1 ocredit=-1password required pam_cracklib.so dcredit=-1 ucredit=-1 ocredit=-1 lcredit=0 minlen=8 enforce_for_root[root@riyimei ~]#

