scemu
特征
- 📦rust safety,对恶意软件有利。
- 所有的依赖都in rust。
- 没有unsafe{}块。
- ⚡非常快的仿真(比unicorn快得多)
- 3 000 000指令/秒
- 100,000条指令/第二次打印每条指令-vv。
- 提供iced-x86 rust反编译器库。
- 迭代检测器
- 内存和寄存器跟踪
- 彩色的
- 在特定的时刻停下来,探索或者修改它
- 105项指示得到执行
- 112个WINAPI实现了5个DLLs
- 所有Linux系统调用
- SEH链
- 向量异常处理程序
- PEB,TEB结构
- 内存分配器
- 与INT 3反应。
- 未调试的cpuid
- 具有已知有效载荷的测试:
- more fpu
- mmx
- 64 bits
- scripting?
```
使用
```shell SCEMU 32bits emulator for Shellcodes 0.2.5 @sha0coder
USAGE: scemu [FLAGS] [OPTIONS]
FLAGS: -e, —endpoint perform communications with the endpoint, use tor or vpn! -h, —help Prints help information -l, —loops show loop interations, it is slow. -m, —memory trace all the memory accesses read and write. -n, —nocolors print without colors for redirectin to a file >out -r, —regs print the register values in every step. -V, —version Prints version information -v, —verbose -vv for view the assembly, -v only messages, without verbose only see the api calls and goes faster
OPTIONS: -b, —base
set base address for code -c, —console
```shell用于 Shellcodes 0.2.5 的 SCEMU 32 位仿真器@sha0coder用法:scemu [标志] [选项]标志:-e, --endpoint 与端点进行通信,使用tor或vpn-h, --help 打印帮助信息-l, --loops 显示循环交互,它很慢-m, --memory 跟踪所有内存访问读写-n, --nocolors 打印不带颜色以重定向到文件 >out-r, --regs 打印每一步的寄存器值-V, --version 打印版本信息-v, --verbose -vv 用于查看程序集,-v 仅消息选项:-b, --base <ADDRESS> 设置代码的基地址-c, --console <NUMBER> 选择在哪个时刻生成要检查的控制台-C, --console_addr <ADDRESS> 在第一个 eip = 地址上生成控制台-a, --entry <ADDRESS> shellcode的入口点,默认从头开始-f, --filename <FILE> 设置 shellcode 二进制文件-i, --inspect <DIRECTION> 监控内存,例如:-i 'dword ptr [ebp + 0x24]-M, --maps <PATH> 选择内存映射文件夹-R, --reg <REGISTER> 在每一步跟踪一个特定的寄存器,值和内容-s, --string <ADDRESS> 监控特定地址上的字符串
一些用例
Scemu模拟一个检测execve()中断的简单ShellCode:
我们选择一行停止,并检查内存:
在 linux 中模拟了近 200 万条 GuLoader win32 指令后,伪装 cpuid 和其他技巧,到达一个 sigtrap(SIG 崩溃) 以混淆调试器:
API加载程序上的内存转储示例:
默认情况下,有几个映射,可以使用像LoadLibrary A这样的API创建更多,也可以从控制台手动创建:
基于打印消息的LdrLoadDLl()仿真基本WindowsShellCode:
控制台允许查看CPU当前状态的编辑:
--- console ---=>h--- help ---q ...................... quitcls .................... clear screenh ...................... helps ...................... stackv ...................... varsr ...................... register show allr reg .................. show regrc ..................... register changef ...................... show all flagsfc ..................... clear all flagsfz ..................... toggle flag zerofs ..................... toggle flag signc ...................... continueba ..................... breakpoint on addressbi ..................... breakpoint on instruction numberbmr .................... breakpoint on read memorybmw .................... breakpoint on write memorybc ..................... clear breakpointn ...................... next instructioneip .................... change eippush ................... push dword to the stackpop .................... pop dword from stackfpu .................... fpu viewmd5 .................... check the md5 of a memory mapseh .................... view SEHveh .................... view vectored execption pointerm ...................... memory mapsma ..................... memory allocsmc ..................... memory create mapmn ..................... memory name of an addressml ..................... memory load file content to mapmr ..................... memory read, speficy ie: dword ptr [esi]mw ..................... memory read, speficy ie: dword ptr [esi] and then: 1afmd ..................... memory dumpmrd .................... memory read dwordsmds .................... memory dump stringmdw .................... memory dump wide stringmdd .................... memory dump to diskmt ..................... memory testss ..................... search stringsb ..................... search bytessba .................... search bytes in all the mapsssa .................... search string in all the mapsll ..................... linked list walkd ...................... dissasembledt ..................... dump structureenter .................. step into
q ......................退出cls ....................清除屏幕h ......................帮助s ......................堆栈v ......................变量r ......................注册 显示所有r reg ..................显示 regrc .....................注册更改f ......................显示所有标志fc .....................清除所有标志fz .....................切换标志为零fs .....................切换标志符号c ......................继续ba .....................地址上的断点bi .....................指令号上的断点bmr ....................读内存断点bmw ....................写入内存的断点bc .....................清除断点n ......................下一条指令eip ....................更改eippush ...................将 dword 推入堆栈pop ....................从堆栈中弹出 dwordfpu ....................fpu 视图md5 ....................检查内存映射的md5seh ....................查看 SEHveh ....................查看向量执行指针m ......................内存映射ma .....................内存分配mc .....................内存创建映射mn .....................地址的内存名称ml .....................内存加载文件内容到映射mr .....................内存读取,特别是:dword ptr [esi]mw .....................内存读取,特别是:dword ptr [esi] 然后:1afmd .....................内存转储mrd ....................内存读取 dwordsmds ....................内存转储字符串mdw ....................内存转储宽字符串mdd ....................内存转储到磁盘mt .....................内存测试ss .....................搜索字符串sb .....................搜索字节sba ....................在所有映射中搜索字节ssa ....................在所有地图中搜索字符串ll .....................链表遍历d ......................拆卸dt .....................转储结构enter ..................步入
Cobalt Strike API加载程序与Metasploit相同,并模拟它:
Cobalt Strike的API调用:
Metasploit rshell的API调用: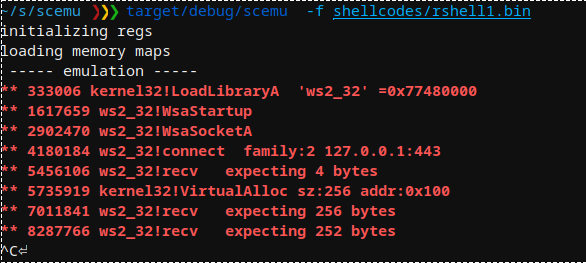
Metasploit SGN编码器使用少量FPU隐藏多态性:
Metasploit shikata-ga-nai编码器,也以FPU开头:
显示PEB结构:
=>dtstructure=>pebaddress=>0x7ffdf000PEB {reserved1: [0x0,0x0,],being_debugged: 0x0,reserved2: 0x0,reserved3: [0xffffffff,0x400000,],ldr: 0x77647880,process_parameters: 0x2c1118,reserved4: [0x0,0x2c0000,0x77647380,],alt_thunk_list_ptr: 0x0,reserved5: 0x0,reserved6: 0x6,reserved7: 0x773cd568,reserved8: 0x0,alt_thunk_list_ptr_32: 0x0,reserved9: [0x0,...
显示PEBLDR数据结构:
=>dtstructure=>PEB_LDR_DATAaddress=>0x77647880PebLdrData {length: 0x30,initializated: 0x1,sshandle: 0x0,in_load_order_module_list: ListEntry {flink: 0x2c18b8,blink: 0x2cff48,},in_memory_order_module_list: ListEntry {flink: 0x2c18c0,blink: 0x2cff50,},in_initialization_order_module_list: ListEntry {flink: 0x2c1958,blink: 0x2d00d0,},entry_in_progress: ListEntry {flink: 0x0,blink: 0x0,},}=>
显示LDR_DATA_TABLE_ENTRY和第一个模块名
=>dtstructure=>LDR_DATA_TABLE_ENTRYaddress=>0x2c18c0LdrDataTableEntry {reserved1: [0x2c1950,0x77647894,],in_memory_order_module_links: ListEntry {flink: 0x0,blink: 0x0,},reserved2: [0x0,0x400000,],dll_base: 0x4014e0,entry_point: 0x1d000,reserved3: 0x40003e,full_dll_name: 0x2c1716,reserved4: [0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,],reserved5: [0x17440012,0x4000002c,0xffff0000,],checksum: 0x1d6cffff,reserved6: 0xa640002c,time_date_stamp: 0xcdf27764,}=>
恶意软件在异常中隐藏了一些东西:
3307726 0x4f9673: push ebp3307727 0x4f9674: push edx3307728 0x4f9675: push eax3307729 0x4f9676: push ecx3307730 0x4f9677: push ecx3307731 0x4f9678: push 4F96F4h3307732 0x4f967d: push dword ptr fs:[0]Reading SEH 0x0-------3307733 0x4f9684: mov eax,[51068Ch]--- console ---=>
检查异常结构:
--- console ---=>r espesp: 0x22de98=>dtstructure=>cppeh_recordaddress=>0x22de98CppEhRecord {old_esp: 0x0,exc_ptr: 0x4f96f4,next: 0xfffffffe,exception_handler: 0xfffffffe,scope_table: PScopeTableEntry {enclosing_level: 0x278,filter_func: 0x51068c,handler_func: 0x288,},try_level: 0x288,}=>
这里我们有错误例程0x4f96f4和过滤器0x51068c。

